Category: Securityaffairs
Omni Family Health data breach impacts 468,344 individuals Pierluigi Paganini October 19, 2024 Omni Family Health disclosed a data breach…
Iran-linked actors target critical infrastructure organizations Pierluigi Paganini October 18, 2024 U.S. and allies warn of attacks from Iran-linked actors…
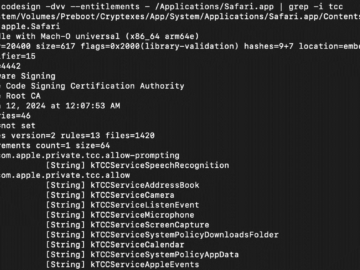
macOS HM Surf flaw in TCC allows bypass Safari privacy settings Pierluigi Paganini October 18, 2024 Microsoft disclosed a flaw…
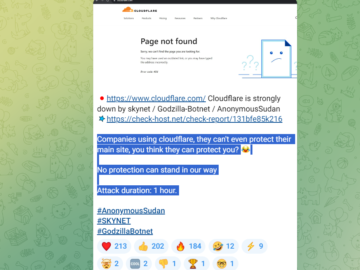
Two Sudanese nationals indicted for operating the Anonymous Sudan group Pierluigi Paganini October 18, 2024 The DoJ charged Anonymous Sudan…
Russia-linked RomCom group targeted Ukrainian government agencies since late 2023 Pierluigi Paganini October 17, 2024 Russia-linked threat actor RomCom targeted…
A critical flaw in Kubernetes Image Builder could allow attackers to gain root access Pierluigi Paganini October 17, 2024 A…
VMware fixes high-severity SQL injection flaw CVE-2024-38814 in HCX Pierluigi Paganini October 17, 2024 VMware fixes a high-severity SQL injection…
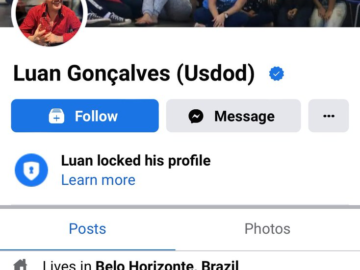
Brazil’s Polícia Federal arrested the notorious hacker USDoD Pierluigi Paganini October 16, 2024 Brazil’s Polícia Federal has arrested hacker USDoD,…
Finnish Customs dismantled the dark web drugs market Sipulitie Pierluigi Paganini October 16, 2024 Finnish Customs shut down the Tor…
U.S. CISA adds Microsoft Windows Kernel, Mozilla Firefox and SolarWinds Web Help Desk bugs to its Known Exploited Vulnerabilities catalog Pierluigi…
GitHub addressed a critical vulnerability in Enterprise Server Pierluigi Paganini October 16, 2024 GitHub addressed a critical vulnerability in Enterprise…
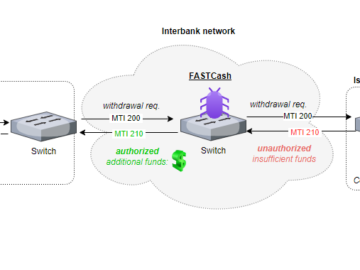
A new Linux variant of FASTCash malware targets financial systems Pierluigi Paganini October 15, 2024 North Korea-linked actors deploy a…