Category: Securityaffairs
8Base ransomware operators use a new variant of the Phobos ransomware Pierluigi Paganini November 19, 2023 8Base ransomware operators were observed…
Israeli man sentenced to 80 months in prison for providing hacker-for-hire services Pierluigi Paganini November 18, 2023 An Israeli hacker…
Russian APT Gamaredon uses USB worm LitterDrifter against Ukraine Pierluigi Paganini November 18, 2023 Russia-linked cyberespionage group Gamaredon has been…
The board of directors of OpenAI fired Sam Altman Pierluigi Paganini November 17, 2023 OpenAI fired its CEO Sam Altman,…
Medusa ransomware gang claims the hack of Toyota Financial Services Pierluigi Paganini November 17, 2023 Toyota Financial Services discloses unauthorized…
A critical OS command injection flaw affects Fortinet FortiSIEM Pierluigi Paganini November 17, 2023 Fortinet warns of a critical OS…
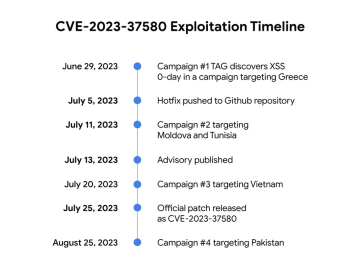
Zimbra zero-day exploited to steal government emails by four groups Pierluigi Paganini November 16, 2023 Google TAG revealed that threat…
Vietnam Post exposes 1.2TB of data, including email addresses Pierluigi Paganini November 16, 2023 Vietnam Post Corporation, a Vietnamese government-owned…
Samsung suffered a new data breach Pierluigi Paganini November 16, 2023 Samsung Electronics disclosed a data breach that exposed customer…
FBI and CISA warn of attacks by Rhysida ransomware gang Pierluigi Paganini November 16, 2023 The FBI and CISA warn…
Critical flaw fixed in SAP Business One product Pierluigi Paganini November 15, 2023 Enterprise software giant SAP addressed a critical…
Law enforcement agencies dismantled the illegal botnet proxy service IPStorm Pierluigi Paganini November 15, 2023 The Federal Bureau of Investigation…