Category: Securityaffairs
Dolly.com pays ransom, attackers release data anyway Pierluigi Paganini November 10, 2023 On-demand moving and delivery platform Dolly.com allegedly paid…
DDoS attack leads to significant disruption in ChatGPT services Pierluigi Paganini November 09, 2023 OpenAI confirmed that the outage suffered…
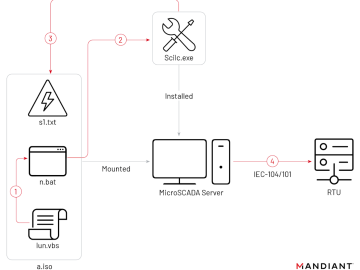
Russian Sandworm disrupts power in Ukraine with a new OT attack Pierluigi Paganini November 09, 2023 Mandiant reported that Russia-linked…
CISA adds SLP flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini November 09, 2023 US CISA added the vulnerability CVE-2023-29552…
The largest Russian bank Sberbank hit by a massive DDoS attack Pierluigi Paganini November 09, 2023 The largest and oldest…
Sumo Logic discloses security breach and recommends customers rotate credentials Pierluigi Paganini November 08, 2023 Security firm Sumo Logic disclosed…
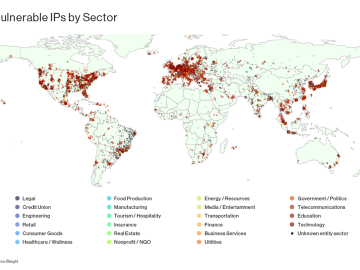
FBI: Ransomware actors abuse third parties and legitimate system tools for initial access Pierluigi Paganini November 08, 2023 The FBI…
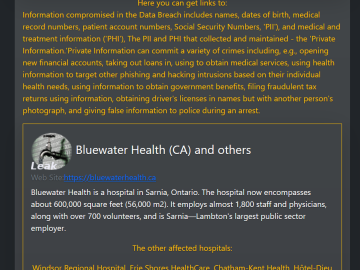
Five Canadian Hospitals impacted by a ransomware attack on TransForm provider Pierluigi Paganini November 08, 2023 Five Canadian hospitals were…
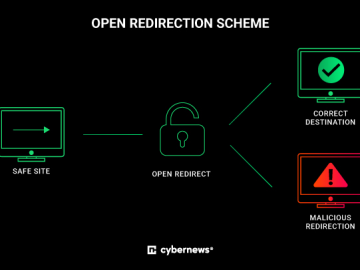
Royal Mail jeopardizes users with open redirect flaw Pierluigi Paganini November 08, 2023 Royal Mail has left an open redirect…
North Korea-linked APT BlueNoroff used new macOS malware ObjCShellz Pierluigi Paganini November 08, 2023 The North Korea-linked APT BlueNoroff used a…
Marina Bay Sands Luxury Hotel in Singapore Suffers a Data Breach Pierluigi Paganini November 07, 2023 The iconic integrated resort…
Veeam fixed multiple flaws in Veeam ONE, including critical issues Pierluigi Paganini November 07, 2023 Veeam addressed multiple vulnerabilities in…