Category: Securityaffairs
CISA adds Adobe Acrobat Reader flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini October 11, 2023 US CISA added…
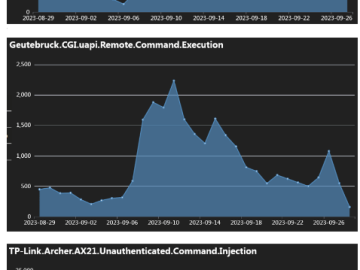
Mirai-based DDoS botnet IZ1H9 added 13 payloads to target routers Pierluigi Paganini October 11, 2023 A Mirai-based DDoS botnet tracked…
Air Europa data breach exposed customers’ credit cards Pierluigi Paganini October 11, 2023 Airline Air Europa disclosed a data breach…
#OpIsrael, #FreePalestine & #OpSaudiArabia – How Cyber Actors Capitalize On War Actions Via Psy-Ops Pierluigi Paganini October 11, 2023 Gaza:…
Microsoft Patch Tuesday updates for October 2023 fixed three actively exploited zero-day flaws Pierluigi Paganini October 11, 2023 Microsoft Patch…
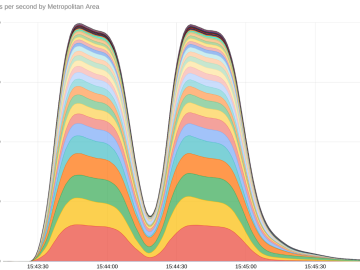
New ‘HTTP/2 Rapid Reset’ technique behind record-breaking DDoS attacks Pierluigi Paganini October 10, 2023 A new DDoS technique named ‘HTTP/2…
A flaw in libcue library impacts GNOME Linux systems Pierluigi Paganini October 10, 2023 A vulnerability in the libcue library…
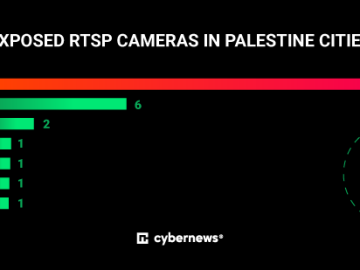
Exposed security cameras in Israel and Palestine pose significant risks Pierluigi Paganini October 10, 2023 Many poorly configured security cameras…
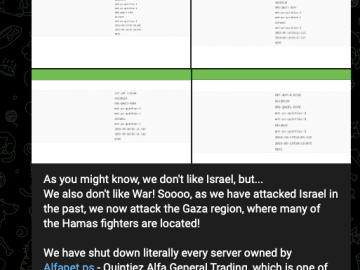
Hacktivists in Palestine and Israel after SCADA and other industrial control systems Pierluigi Paganini October 10, 2023 Both pro-Israeli and…
Large-scale Citrix NetScaler Gateway credential harvesting campaign exploits CVE-2023-3519 Pierluigi Paganini October 09, 2023 IBM observed a credential harvesting campaign…
The source code of the 2020 variant of HelloKitty ransomware was leaked on a cybercrime forum Pierluigi Paganini October 09,…
Gaza-linked hackers and Pro-Russia groups are targeting Israel Pierluigi Paganini October 09, 2023 Microsoft linked a Gaza-based threat actor tracked…