Category: TheCyberExpress
2024 was a difficult year for healthcare cybersecurity, but there are some hopeful signs heading into 2025, with effective controls…
The rise of Application Programming Interfaces (APIs) has revolutionized how businesses operate, enabling seamless connectivity, data sharing, and enhanced functionalities…
Cyble dark web researchers have documented a new Russia-linked threat group that has been breaching critical infrastructure environments and tampering…
Last month’s attack on supply chain management platform Blue Yonder has been attributed to a new ransomware group known as…
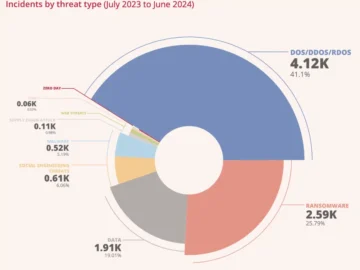
A new report from the European Union Agency for Cybersecurity (ENISA) offers critical insights into the state of European Union…
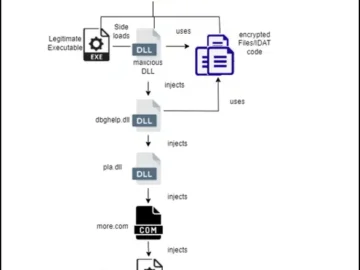
In a recent analysis by Cyble Research and Intelligence Labs (CRIL), a multi-stage cyberattack campaign has been identified, targeting the…
Pro tip for hackers: Don’t threaten people whose specialty is uncovering the identity of cybercriminals. That mistake apparently led to…
The FBI has issued a new warning about the increasing use of artificial intelligence (AI) in online fraud schemes, which…
Black Friday is the best, right? Well, sometimes. Deals everywhere, and chaos too. I’ve had moments feeling so lost in…
Clipper, a decentralized exchange (DEX), became the target of a cyberattack that led to a loss of approximately $450,000 from…
Zyxel Firewalls have become a key target in recent cyberattacks, with attackers exploiting a critical vulnerability to deploy the dangerous…
Oracle’s Agile Product Lifecycle Management (PLM) software has been flagged for a security vulnerability (CVE-2024-21287) by CERT-In (Computer Emergency Response Team…