Category: TheHackerNews
Apr 27, 2025Ravie LakshmananKubernetes / Cloud Security Microsoft has revealed that a threat actor it tracks as Storm-1977 has conducted…
Apr 26, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have detailed the activities of an initial access broker (IAB) dubbed ToyMaker…
North Korea-linked threat actors behind the Contagious Interview have set up front companies as a way to distribute malware during…
When we talk about identity in cybersecurity, most people think of usernames, passwords, and the occasional MFA prompt. But lurking…
Apr 25, 2025Ravie LakshmananVulnerability / Enterprise Security Threat actors are likely exploiting a new vulnerability in SAP NetWeaver to upload…
Apr 25, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers are warning about a new malware called DslogdRAT that’s installed following…
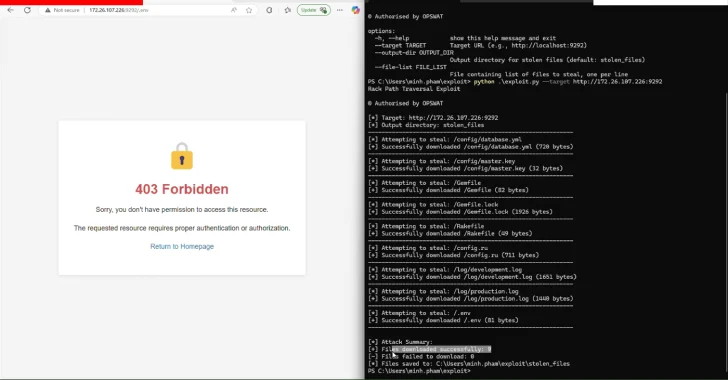
Apr 25, 2025Ravie LakshmananVulnerability / Data Breach Cybersecurity researchers have disclosed three security flaws in the Rack Ruby web server…
Apr 24, 2025Ravie LakshmananMalware / Threat Intelligence At least six organizations in South Korea have been targeted by the prolific…
Apr 24, 2025Ravie LakshmananEndpoint Security / Linux Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a…
Apr 24, 2025Ravie LakshmananVulnerability / Threat Intelligence As many as 159 CVE identifiers have been flagged as exploited in the…
Apr 24, 2025Ravie LakshmananPhishing / Cybercrime The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to…
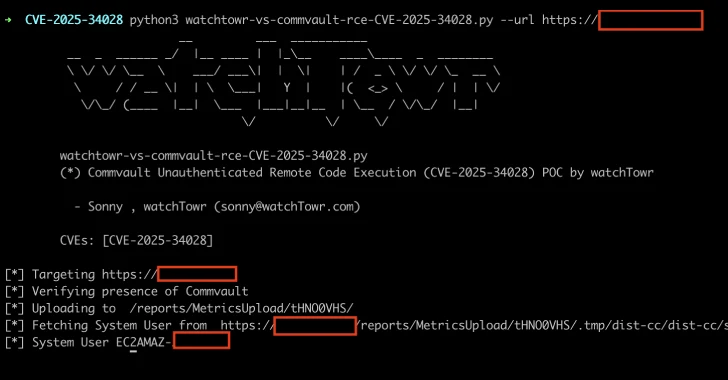
Apr 24, 2025Ravie LakshmananData Breach / Vulnerability A critical security flaw has been disclosed in the Commvault Command Center that…