Category: TheHackerNews
As SaaS and cloud-native work reshape the enterprise, the web browser has emerged as the new endpoint. However, unlike endpoints,…
Apr 22, 2025Ravie LakshmananIdentity Management / Cloud Security Microsoft on Monday announced that it has moved the Microsoft Account (MSA)…
Apr 22, 2025Ravie LakshmananCyber Espionage / Threat Intelligence The China-linked cyber espionage group tracked as Lotus Panda has been attributed…
Apr 21, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored…
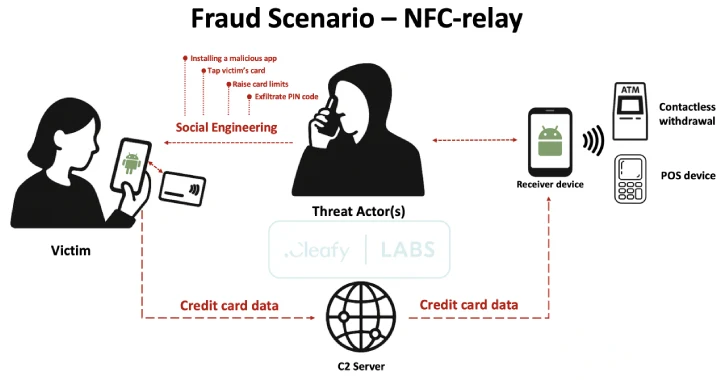
Apr 21, 2025Ravie LakshmananTechnology / Mobile Security A new Android malware-as-a-service (MaaS) platform named SuperCard X can facilitate near-field communication…
The problem is simple: all breaches start with initial access, and initial access comes down to two primary attack vectors…
Apr 21, 2025Ravie LakshmananVulnerability / Threat Intelligence Cybersecurity researchers have disclosed a surge in “mass scanning, credential brute-forcing, and exploitation…
The Russian state-sponsored threat actor known as APT29 has been linked to an advanced phishing campaign that’s targeting diplomatic entities…
Apr 19, 2025Ravie LakshmananLinux / Malware Cybersecurity researchers have uncovered three malicious packages in the npm registry that masquerade as…
Apr 19, 2025Ravie LakshmananNetwork Security / Vulnerability ASUS has disclosed a critical security flaw impacting routers with AiCloud enabled that…
Cybersecurity researchers are warning of a “widespread and ongoing” SMS phishing campaign that’s been targeting toll road users in the…
A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader. “Attackers increasingly…