Category: TheHackerNews
Apr 16, 2025Ravie LakshmananArtificial Intelligence / Malvertising Google on Wednesday revealed that it suspended over 39.2 million advertiser accounts in…
Threat actors are leveraging an artificial intelligence (AI) powered presentation platform named Gamma in phishing attacks to direct unsuspecting users…
Intro: Why hack in when you can log in? SaaS applications are the backbone of modern organizations, powering productivity and…
Apr 16, 2025Ravie LakshmananCyber Espionage / Network Security Cybersecurity researchers have unearthed a new controller component associated with a known…
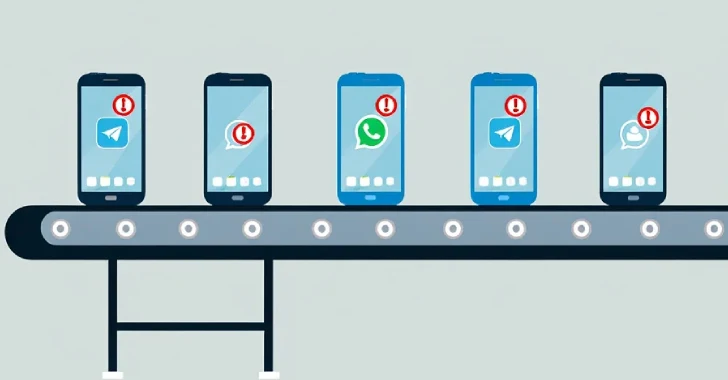
Cheap Android smartphones manufactured by Chinese companies have been observed pre-installed with trojanized apps masquerading as WhatsApp and Telegram that…
Apr 16, 2025Ravie LakshmananVulnerability Management / Incident Response The U.S. government funding for non-profit research giant MITRE to operate and…
Apr 15, 2025Ravie LakshmananSupply Chain Attack / Malware Cybersecurity researchers have disclosed a malicious package uploaded to the Python Package…
Apr 15, 2025Ravie LakshmananVulnerability / Software Security A critical security vulnerability has been disclosed in the Apache Roller open-source, Java-based…
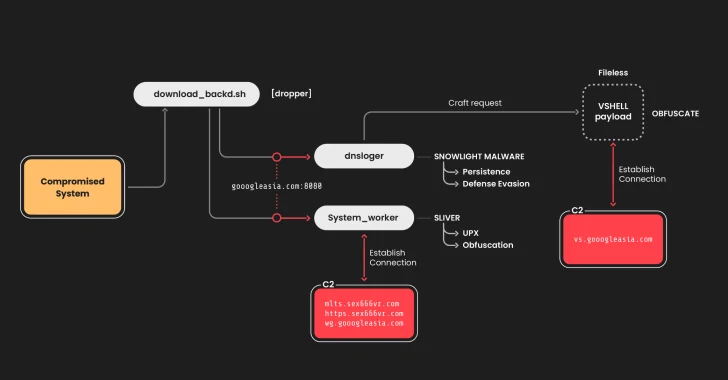
Apr 15, 2025Ravie LakshmananLinux / Malware The China-linked threat actor known as UNC5174 has been attributed to a new campaign…
Apr 15, 2025The Hacker NewsData Privacy / Enterprise Security Everybody knows browser extensions are embedded into nearly every user’s daily…
The North Korea-linked threat actor assessed to be behind the massive Bybit hack in February 2025 has been linked to…
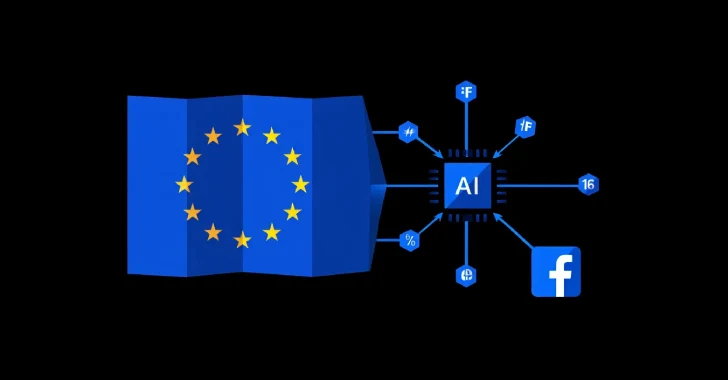
Apr 15, 2025Ravie LakshmananArtificial Intelligence / Data Privacy Meta has announced that it will begin to train its artificial intelligence…