Category: TheHackerNews
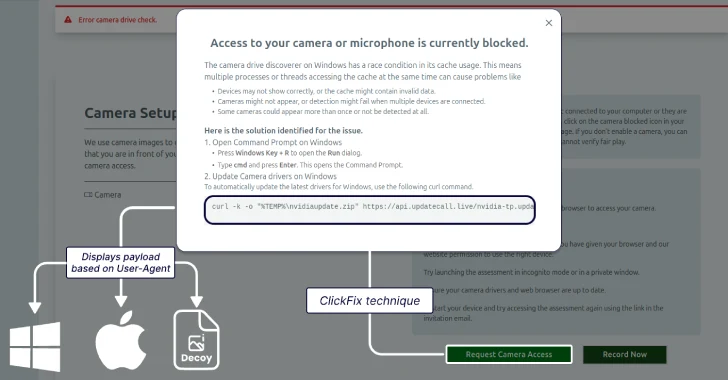
The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job…
Apr 03, 2025The Hacker News The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But…
Apr 03, 2025Ravie LakshmananData Privacy / Vulnerability Cybersecurity researchers have disclosed details of a new vulnerability impacting Google’s Quick Share…
Apr 03, 2025Ravie LakshmananThreat Intelligence / Mobile Security Counterfeit versions of popular smartphone models that are sold at reduced prices…
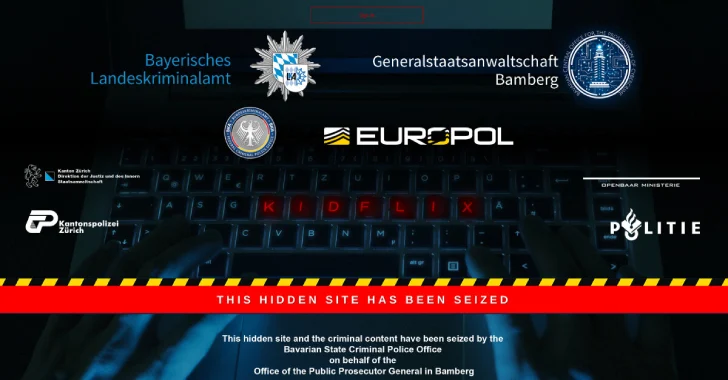
In one of the largest coordinated law enforcement operations, authorities have dismantled Kidflix, a streaming platform that offered child sexual…
Apr 03, 2025Ravie LakshmananCybersecurity / Threat Intelligence Threat hunters are warning of a sophisticated web skimmer campaign that leverages a…
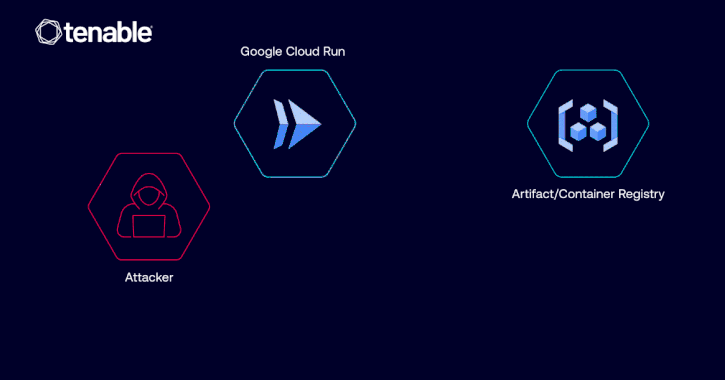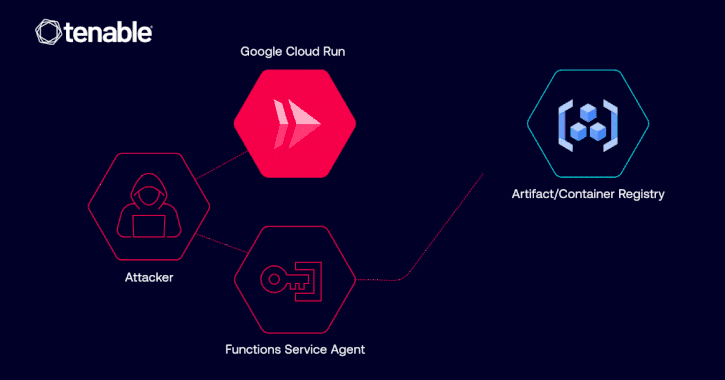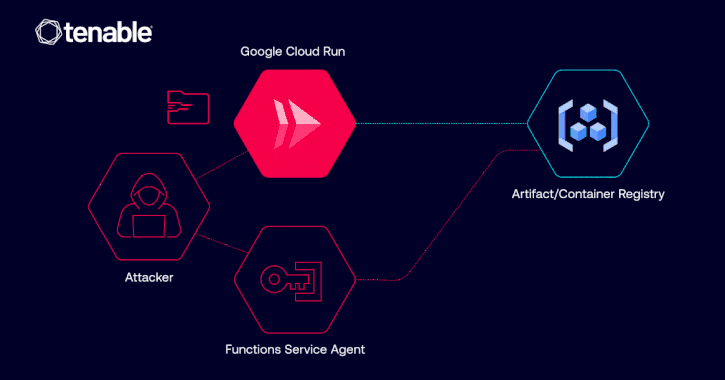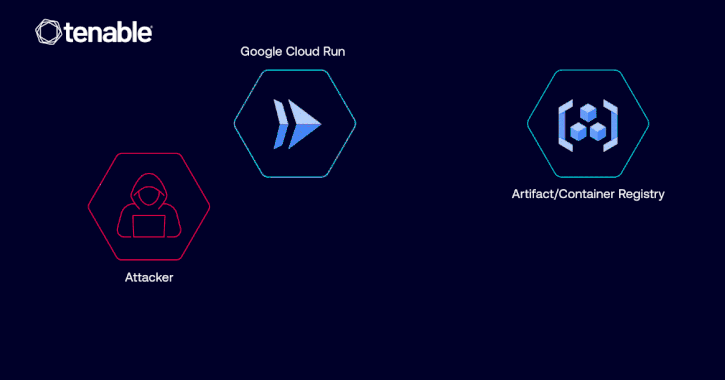
Apr 02, 2025Ravie LakshmananCloud Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched privilege escalation vulnerability in Google…
Apr 02, 2025Ravie LakshmananCryptojacking / Malware Cybersecurity researchers have shed light on an “auto-propagating” cryptocurrency mining botnet called Outlaw (aka…
Apr 02, 2025The Hacker NewsCompliance / Data Protection Introduction As the cybersecurity landscape evolves, service providers play an increasingly vital…
Apr 02, 2025The Hacker NewsWeb Security / Attack Surface When assessing an organization’s external attack surface, encryption-related issues (especially SSL…
Apr 02, 2025Ravie LakshmananRansomware / Email Security The financially motivated threat actor known as FIN7 has been linked to a…
Apr 02, 2025Ravie LakshmananThreat Detection / Malware Cybersecurity researchers have discovered an updated version of a malware loader called Hijack…