Category: TheHackerNews
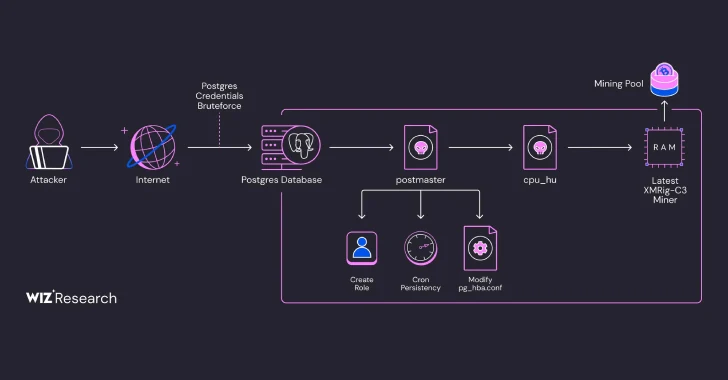
Apr 01, 2025Ravie LakshmananCryptojacking / Cloud Security Exposed PostgreSQL instances are the target of an ongoing campaign designed to gain…
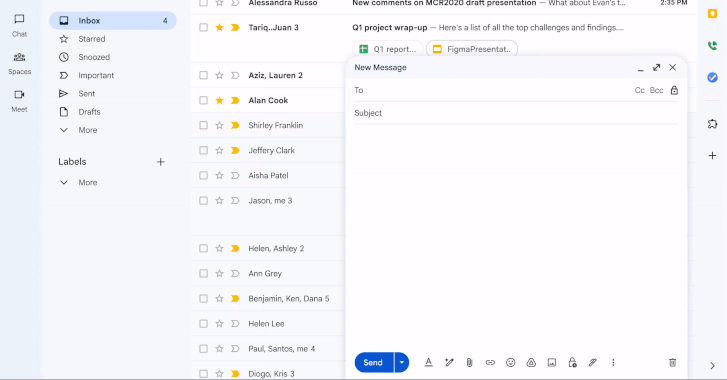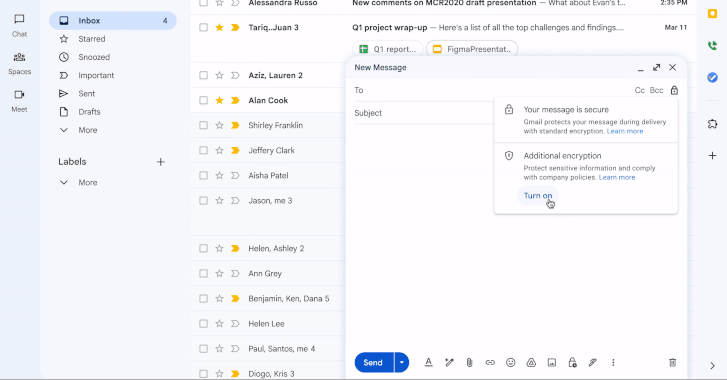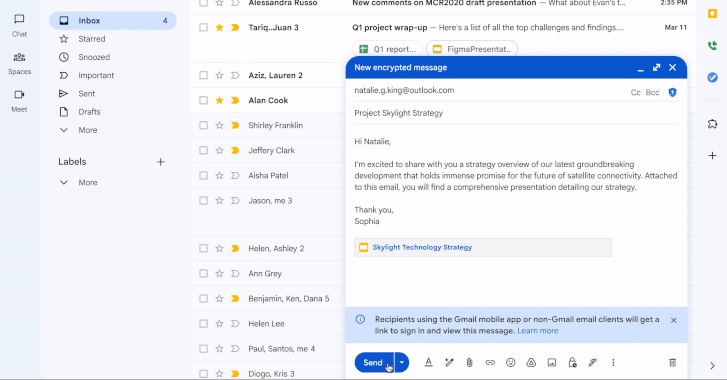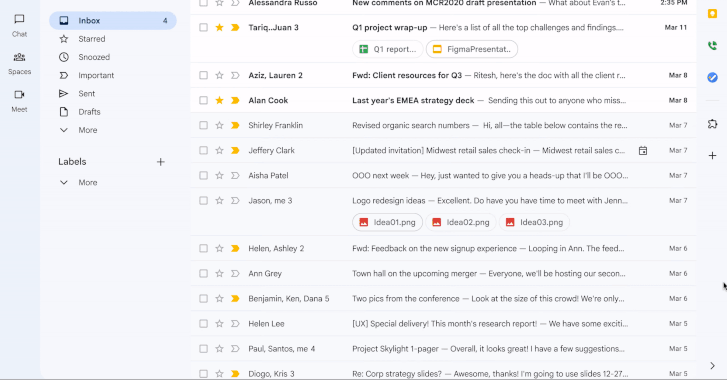
Apr 01, 2025Ravie LakshmananEncryption / Email Security On the 21st birthday of Gmail, Google has announced a major update that…
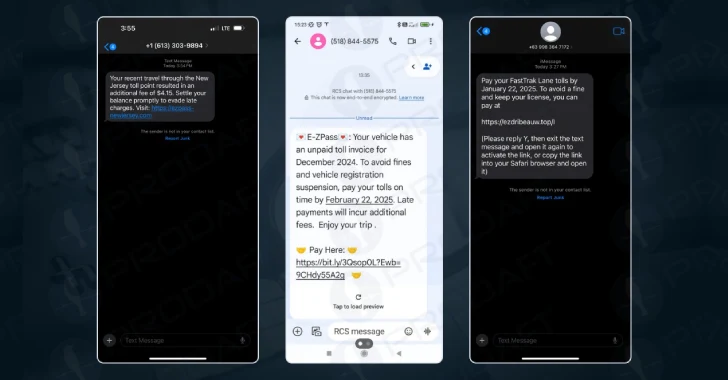
A new sophisticated phishing-as-a-service (PhaaS) platform called Lucid has targeted 169 entities in 88 countries using smishing messages propagated via…
Cybersecurity researchers have shed light on a new China-linked threat actor called Earth Alux that has targeted various key sectors…
Apr 01, 2025The Hacker NewsWeb Security / GDPR Compliance Are your security tokens truly secure? Explore how Reflectiz helped a…
Apr 01, 2025Ravie LakshmananNetwork Security / Vulnerability Cybersecurity researchers are warning of a spike in suspicious login scanning activity targeting…
Apr 01, 2025Ravie LakshmananMobile Security / Vulnerability Apple on Monday backported fixes for three vulnerabilities that have come under active…
Apr 01, 2025Ravie LakshmananData Protection / Privacy Apple has been hit with a fine of €150 million ($162 million) by…
The threat actors behind the zero-day exploitation of a recently-patched security vulnerability in Microsoft Windows have been found to deliver…
Mar 31, 2025Ravie LakshmananData Theft / Website Security Threat actors are using the “mu-plugins” directory in WordPress sites to conceal…
Mar 31, 2025The Hacker NewsIntrusion Detection / Vulnerability If you’re using AWS, it’s easy to assume your cloud security is…
Mar 31, 2025Ravie LakshmananThreat Intelligence / Malware Entities in Ukraine have been targeted as part of a phishing campaign designed…