Category: TheHackerNews
Mar 30, 2025Ravie LakshmananVulnerability / Zero-Day The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has shed light on a new…
Mar 29, 2025Ravie LakshmananThreat Intelligence / Mobile Security Cybersecurity researchers have discovered a new Android banking malware called Crocodilus that’s…
Mar 29, 2025Ravie LakshmananCybercrime / Vulnerability In what’s an instance of hacking the hackers, threat hunters have managed to infiltrate…
Mar 28, 2025Ravie LakshmananOperational Technology / Vulnerability Cybersecurity researchers have disclosed 46 new security flaws in products from three solar…
Mar 28, 2025Ravie LakshmananEndpoint Security / Threat Intelligence Cybersecurity researchers are calling attention to a new sophisticated malware called CoffeeLoader…
Long gone are the days when a simple backup in a data center was enough to keep a business secure….
Mar 28, 2025Ravie LakshmananSpyware / Malware An Android malware family previously observed targeting Indian military personnel has been linked to…
Mar 28, 2025Ravie LakshmananZero-Day / Browser Security Mozilla has released updates to address a critical security flaw impacting its Firefox…
Mar 28, 2025Ravie LakshmananCryptocurrency / Developer Security Cybersecurity researchers have discovered several cryptocurrency packages on the npm registry that have…
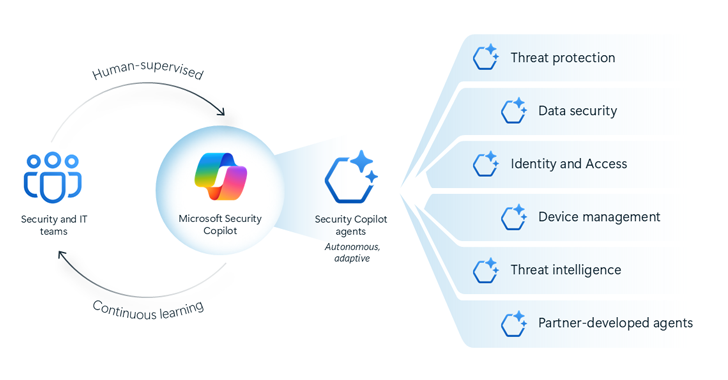
Mar 24, 2025Ravie LakshmananEnterprise Security / Browser Security Microsoft on Monday announced a new feature called inline data protection for…
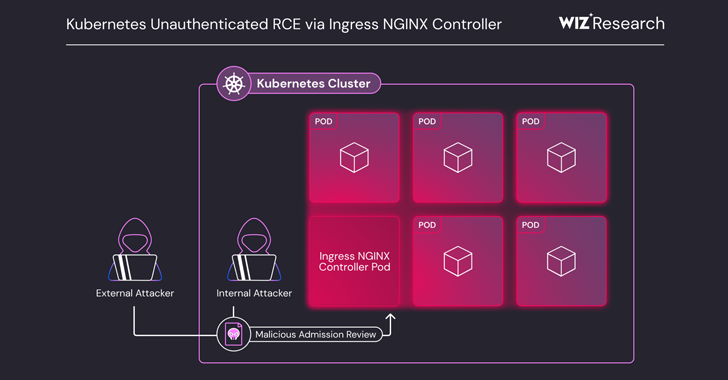
Mar 24, 2025Ravie LakshmananVulnerability / Cloud Security A set of five critical security shortcomings have been disclosed in the Ingress…
Law enforcement authorities in seven African countries have arrested 306 suspects and confiscated 1,842 devices as part of an international…