Category: TheHackerNews
Mar 18, 2025Ravie LakshmananCloud Security / Enterprise Security Google is making the biggest ever acquisition in its history by purchasing…
Mar 18, 2025Ravie LakshmananVulnerability / Windows Security An unpatched security flaw impacting Microsoft Windows has been exploited by 11 state-sponsored…
Mar 18, 2025Ravie LakshmananAd Fraud / Mobile Security Cybersecurity researchers have warned about a large-scale ad fraud campaign that has…
Mar 18, 2025Ravie LakshmananCyber Attack / Malware At least four different threat actors have been identified as involved in an…
Mar 18, 2025Ravie LakshmananCyber Espionage / Malware Threat hunters have shed more light on a previously disclosed malware campaign undertaken…
Mar 18, 2025The Hacker NewsAuthentication / Identity Security While Okta provides robust native security features, configuration drift, identity sprawl, and…
Microsoft is calling attention to a novel remote access trojan (RAT) named StilachiRAT that it said employs advanced techniques to…
Mar 17, 2025Ravie LakshmananVulnerability / Web Security A recently disclosed security flaw impacting Apache Tomcat has come under active exploitation…
Mar 17, 2025Ravie LakshmananWeb Security / Cyber Threat Malicious actors are exploiting Cascading Style Sheets (CSS), which are used to…
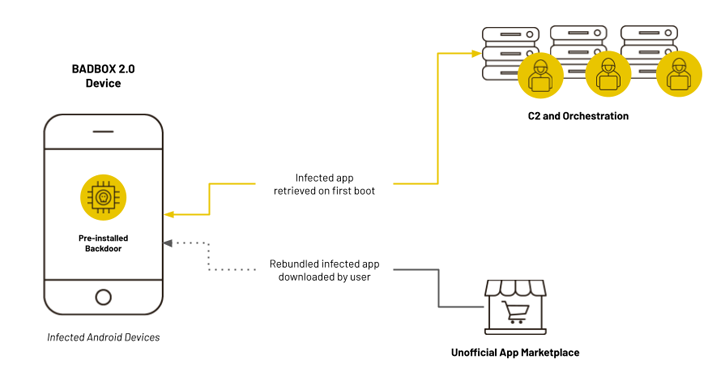
Mar 17, 2025Ravie LakshmananBotnet / Vulnerability An unpatched security flaw impacting the Edimax IC-7100 network camera is being exploited by…
Mar 17, 2025The Hacker NewsCloud Security / Threat Intelligence The latest Palo Alto Networks Unit 42 Cloud Threat Report found…
Mar 17, 2025Ravie LakshmananVulnerability / Cloud Security Cybersecurity researchers are calling attention to an incident in which the popular GitHub…