Category: TheHackerNews
Mar 11, 2025Ravie LakshmananCyber Espionage / Maritime Security Maritime and logistics companies in South and Southeast Asia, the Middle East,…
Mar 11, 2025Ravie LakshmananEnterprise Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added five security…
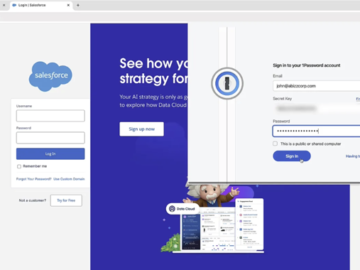
Mar 10, 2025Ravie LakshmananCybersecurity / Malware Cybersecurity researchers have demonstrated a novel technique that allows a malicious web browser extension…
Mar 10, 2025Ravie LakshmananData Theft / Cryptocurrency The Middle East and North Africa have become the target of a new…
The Need For Unified Security Google Workspace is where teams collaborate, share ideas, and get work done. But while it…
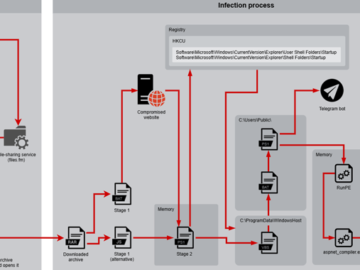
Mar 10, 2025Ravie LakshmananThreat Intelligence / Cybercrime A new mass malware campaign is infecting users with a cryptocurrency miner named…
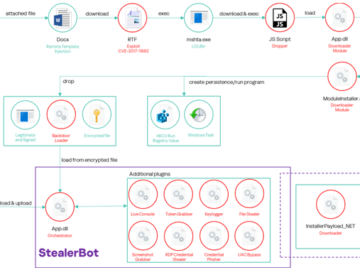
Mar 07, 2025Ravie Lakshmanan Threat hunters have shed light on a “sophisticated and evolving malware toolkit” called Ragnar Loader that’s…
Mar 07, 2025Ravie LakshmananMalvertising / Open Source Microsoft has disclosed details of a large-scale malvertising campaign that’s estimated to have…
Mar 07, 2025The Hacker NewsSoftware Security / AppSec Are you tired of dealing with outdated security tools that never seem…
Mar 07, 2025The Hacker NewsPayment Security / Compliance Access on-demand webinar here Avoid a $100,000/month Compliance Disaster March 31, 2025:…
Mar 07, 2025Ravie LakshmananCryptocurrency / Ransomware A coalition of international law enforcement agencies has seized the website associated with the…
Mar 07, 2025Ravie LakshmananMalware / Blockchain Cybersecurity researchers have discovered a malicious Python package on the Python Package Index (PyPI)…