Category: TheHackerNews
Mar 03, 2025Ravie LakshmananData Privacy / Compliance The U.K.’s Information Commissioner’s Office (ICO) has opened an investigation into online platforms…
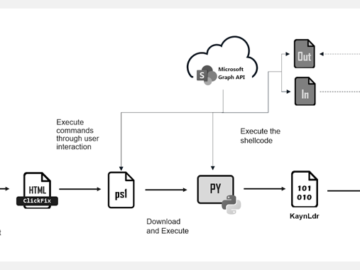
Mar 03, 2025Ravie LakshmananCybercrime / Malware Cybersecurity researchers are calling attention to a new phishing campaign that employs the ClickFix…
In 2024, global ransomware attacks hit 5,414, an 11% increase from 2023. After a slow start, attacks spiked in Q2…
Mar 03, 2025Ravie LakshmananMobile Security / Botnet Brazil, South Africa, Indonesia, Argentina, and Thailand have become the targets of a…
Mar 01, 2025Ravie LakshmananPrivacy / Data Protection Firefox browser maker Mozilla on Friday updated its Terms of Use a second…
Feb 28, 2025Ravie LakshmananMobile Security / Zero-Day A 23-year-old Serbian youth activist had their Android phone targeted by a zero-day…
Cybersecurity researchers have uncovered a widespread phishing campaign that uses fake CAPTCHA images shared via PDF documents hosted on Webflow’s…
Remote Desktop Protocol (RDP) is an amazing technology developed by Microsoft that lets you access and control another computer over…
Feb 28, 2025Ravie LakshmananAPI Security / AI Security Microsoft on Thursday unmasked four of the individuals that it said were…
Feb 28, 2025Ravie LakshmananFinancial Fraud / Cyber Espionage The threat actor known as Sticky Werewolf has been linked to targeted…
A dataset used to train large language models (LLMs) has been found to contain nearly 12,000 live secrets, which allow…
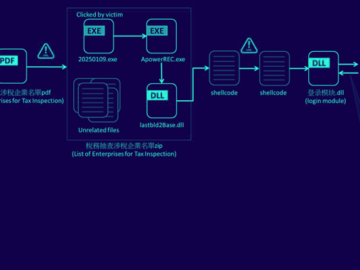
Feb 27, 2025Ravie LakshmananMalware / Threat Intelligence A new campaign is targeting companies in Taiwan with malware known as Winos…