Category: TheHackerNews
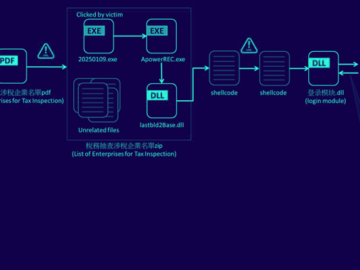
Feb 27, 2025Ravie LakshmananMalware / Threat Intelligence A new campaign is targeting companies in Taiwan with malware known as Winos…
Feb 27, 2025Ravie LakshmananCybercrime / Android Cybersecurity researchers have discovered an updated version of an Android malware called TgToxic (aka…
Feb 27, 2025The Hacker NewsArtificial Intelligence / Browser Security Organizations are either already adopting GenAI solutions, evaluating strategies for integrating…
Feb 27, 2025Ravie LakshmananMalware / Network Security The threat actor known as Space Pirates has been linked to a malicious…
Feb 27, 2025Ravie LakshmananVulnerability / Network Security A new malware campaign has been observed targeting edge devices from Cisco, ASUS,…
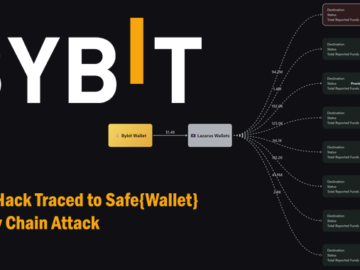
Feb 27, 2025Ravie LakshmananCybercrime / Cryptocurrency The U.S. Federal Bureau of Investigation (FBI) formally linked the record-breaking $1.5 billion Bybit…
Feb 26, 2025Ravie LakshmananEnterprise Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday placed two security…
A cross-site scripting (XSS) vulnerability in a virtual tour framework has been weaponized by malicious actors to inject malicious scripts…
Feb 26, 2025Ravie LakshmananMalware / Cryptocurrency Cybersecurity researchers have flagged a malicious Python library on the Python Package Index (PyPI)…
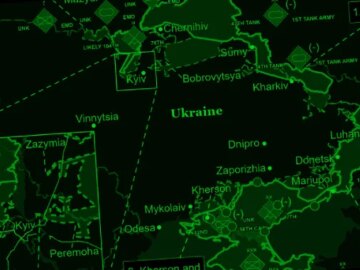
Feb 26, 2025Ravie LakshmananNetwork Security / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday warned of…
Feb 26, 2025The Hacker NewsIdentity Protection / Password Security Passwords are rarely appreciated until a security breach occurs; suffice to…
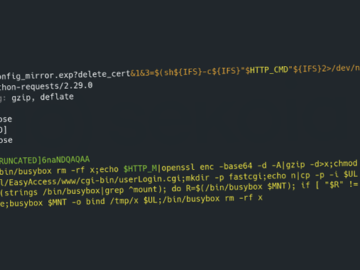
Feb 26, 2025Ravie LakshmananLinux / Endpoint Security Universities and government organizations in North America and Asia have been targeted by…