Category: TheHackerNews
More than a year’s worth of internal chat logs from a ransomware gang known as Black Basta have been published…
Feb 25, 2025Ravie LakshmananMalware / Cyber Espionage Opposition activists in Belarus as well as Ukrainian military and government organizations are…
Cybersecurity researchers have flagged an updated version of the LightSpy implant that comes equipped with an expanded set of data…
Feb 25, 2025Ravie LakshmananGaming / Threat Intelligence Cybersecurity researchers are calling attention to an ongoing campaign that’s targeting gamers and…
Feb 25, 2025Ravie LakshmananWindows Security / Vulnerability A large-scale malware campaign has been found leveraging a vulnerable Windows driver associated…
The first quarter of 2025 has been a battlefield in the world of cybersecurity. Cybercriminals continued launching aggressive new campaigns…
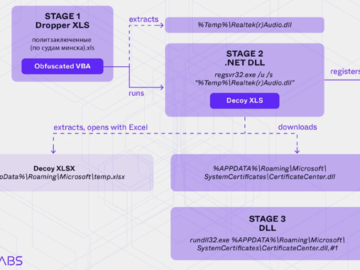
Various industrial organizations in the Asia-Pacific (APAC) region have been targeted as part of phishing attacks designed to deliver a…
Feb 25, 2025Ravie LakshmananNetwork Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws…
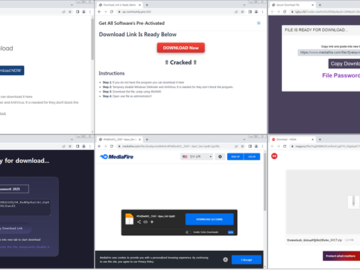
Feb 24, 2025Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers are warning of a new campaign that leverages cracked versions of…
Feb 24, 2025Ravie LakshmananCloud Security / Encryption Google Cloud has announced quantum-safe digital signatures in Google Cloud Key Management Service…
Feb 24, 2025Ravie LakshmananSoftware Security / Data Protection Australia has become the latest country to ban the installation of security…
Feb 22, 2025Ravie LakshmananFinancial Crime / Cryptocurrency Cryptocurrency exchange Bybit on Friday revealed that a “sophisticated” attack led to the…