Category: TheHackerNews
For decades, Microsoft Exchange has been the backbone of business communications, powering emailing, scheduling and collaboration for organizations worldwide. Whether…
Feb 20, 2025Ravie LakshmananSoftware Security / Vulnerability Microsoft has released security updates to address two Critical-rated flaws impacting Bing and…
Feb 20, 2025Ravie LakshmananVulnerability / IT Security Citrix has released security updates for a high-severity security flaw impacting NetScaler Console…
Feb 19, 2025Ravie LakshmananMobile Security / Cyber Espionage Multiple Russia-aligned threat actors have been observed targeting individuals of interest via…
Feb 19, 2025The Hacker NewsMalware / Threat Intelligence A new variant of the Snake Keylogger malware is being used to…
The growing demand for cybersecurity and compliance services presents a great opportunity for Managed Service Providers (MSPs) and Managed Security…
Feb 19, 2025The Hacker NewsWindows Security / Malware Users who are on the lookout for popular games were lured into…
Feb 19, 2025Ravie LakshmananThreat Intelligence / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security…
Feb 18, 2025Ravie LakshmananVulnerability / Network Security Two security vulnerabilities have been discovered in the OpenSSH secure networking utility suite…
Feb 18, 2025Ravie LakshmananCyber Espionage / Malware The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing…
Feb 18, 2025Ravie LakshmananThreat Intelligence / Malware Cybersecurity researchers are alerting to a new campaign that leverages web injects to…
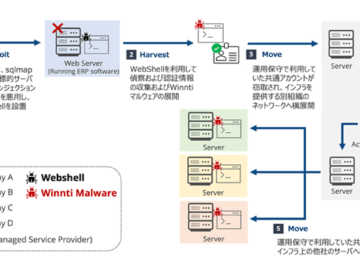
Feb 18, 2025Ravie LakshmananMalware / Network Security The China-linked threat actor known as Winnti has been attributed to a new…