Category: TheHackerNews
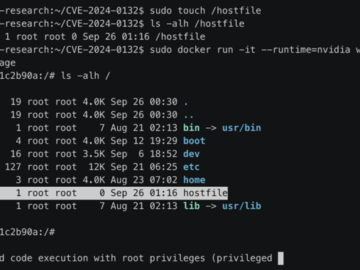
Feb 12, 2025Ravie LakshmananContainer Security / Vulnerability Cybersecurity researchers have discovered a bypass for a now-patched security vulnerability in the…
Feb 12, 2025Ravie LakshmananPatch Tuesday / Vulnerability Microsoft on Tuesday released fixes for 63 security flaws impacting its software products,…
Feb 12, 2025The Hacker NewsAI Security / Data Protection CISOs are finding themselves more involved in AI teams, often leading…
Feb 12, 2025Ravie LakshmananIT Security / Cybercrime The North Korea-linked threat actor known as Kimsuky has been observed using a…
Feb 12, 2025Ravie LakshmananNetwork Security / Vulnerability Ivanti has released security updates to address multiple security flaws impacting Connect Secure…
Feb 11, 2025Ravie LakshmananMobile Security / Machine Learning Google has stepped in to clarify that a newly introduced Android System…
Feb 11, 2025The Hacker NewsIT Security / Threat Protection Multi-factor authentication (MFA) has quickly become the standard for securing business…
Feb 11, 2025The Hacker NewsIoT Security / Cloud Security Gcore’s latest DDoS Radar report analyzes attack data from Q3–Q4 2024,…
Feb 11, 2025Ravie LakshmananNetwork Security / Vulnerability Progress Software has addressed multiple high-severity security flaws in its LoadMaster software that…
Feb 11, 2025Ravie LakshmananMalware / Cyber Attack Threat actors have observed the increasingly common ClickFix technique to deliver a remote…
Feb 11, 2025The Hacker NewsSoftware Security / Threat Intelligence Imagine you’re considering a new car for your family. Before making…
Feb 11, 2025Ravie LakshmananCybercrime / Ransomware Source: The Nation A coordinated law enforcement operation has taken down the dark web…