Category: TheHackerNews
Italy’s data protection watchdog has blocked Chinese artificial intelligence (AI) firm DeepSeek’s service within the country, citing a lack of…
Social engineering has long been an effective tactic because of how it focuses on human vulnerabilities. There’s no brute-force ‘spray…
Jan 31, 2025Ravie LakshmananVulnerability / Data Security Broadcom has released security updates to patch five security flaws impacting VMware Aria…
Over 57 distinct threat actors with ties to China, Iran, North Korea, and Russia have been observed using artificial intelligence…
Jan 30, 2025Ravie LakshmananVulnerability / Cloud Security Cybersecurity researchers have disclosed a critical security flaw in the Lightning AI Studio…
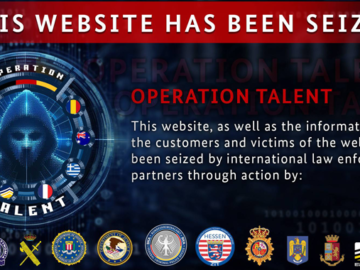
Jan 30, 2025Ravie LakshmananOnline Fraud / Cybercrime An international law enforcement operation has dismantled the domains associated with various online…
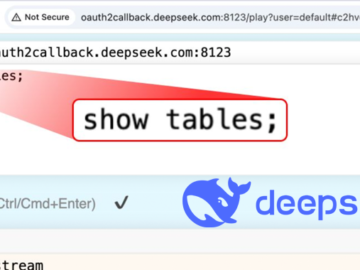
Jan 30, 2025Ravie LakshmananArtificial Intelligence / Data Privacy Buzzy Chinese artificial intelligence (AI) startup DeepSeek, which has had a meteoric…
The job of a SOC analyst has never been easy. Faced with an overwhelming flood of daily alerts, analysts (and…
Jan 30, 2025Ravie LakshmananVulnerability / IoT Security A Mirai botnet variant dubbed Aquabot has been observed actively attempting to exploit…
Jan 30, 2025Ravie LakshmananWeb Security / Vulnerability Three security flaws have been disclosed in the open-source PHP package Voyager that…
Jan 29, 2025Ravie LakshmananThreat Intelligence / Malware The North Korean threat actor known as the Lazarus Group has been observed…
A team of security researchers from Georgia Institute of Technology and Ruhr University Bochum has demonstrated two new side-channel attacks…