Category: TheHackerNews
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday said there are no indications that the cyber attack targeting…
Jan 07, 2025Ravie LakshmananCyber Attack / Hacking Internet service providers (ISPs) and governmental entities in the Middle East have been…
Jan 07, 2025Ravie LakshmananVulnerability / Network Security Taiwan-based Moxa has warned of two security vulnerabilities impacting its cellular routers, secure…
Jan 06, 2025Ravie LakshmananRegulatory Compliance / Data Privacy The Indian government has published a draft version of the Digital Personal…
Jan 06, 2025Ravie LakshmananBlockchain / Malware Cybersecurity researchers have revealed several malicious packages on the npm registry that have been…
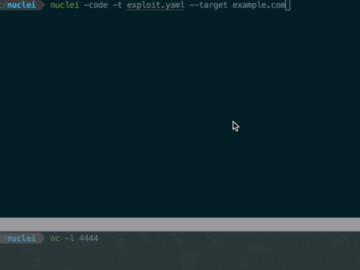
Jan 04, 2025Ravie LakshmananVulnerability / Software Security A high-severity security flaw has been disclosed in ProjectDiscovery’s Nuclei, a widely-used open-source…
Jan 04, 2025Ravie LakshmananMalware / VPN Security Cybersecurity researchers have flagged a new malware called PLAYFULGHOST that comes with a…
Jan 04, 2025Ravie LakshmananCyber Espionage / IoT Botnet The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) on Friday…
Jan 03, 2025Ravie LakshmananMachine Learning / Vulnerability Cybersecurity researchers have shed light on a new jailbreak technique that could be…
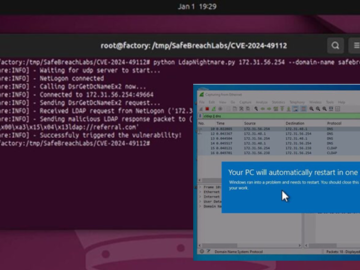
Jan 03, 2025Ravie LakshmananWindows Server / Threat Mitigation A proof-of-concept (PoC) exploit has been released for a now-patched security flaw…
Jan 03, 2025Ravie LakshmananDevOps / Software Development Microsoft has announced that it’s making an “unexpected change” to the way .NET…
Jan 03, 2025Ravie LakshmananTechnology / Data Privacy Apple has agreed to pay $95 million to settle a proposed class action…