Category: TheHackerNews
Dec 18, 2024Ravie LakshmananCyber Espionage / Malware The Russia-linked APT29 threat actor has been observed repurposing a legitimate red teaming…
Having been at ActiveState for nearly eight years, I’ve seen many iterations of our product. However, one thing has stayed…
Dec 18, 2024Ravie LakshmananCyber Fraud / Social engineering INTERPOL is calling for a linguistic shift that aims to put to…
Dec 18, 2024Ravie LakshmananCyber Attack / Vulnerability Threat actors are attempting to exploit a recently disclosed security flaw impacting Apache…
Dec 18, 2024Ravie LakshmananData Breach / Privacy Meta Platforms, the parent company of Facebook, Instagram, WhatsApp, and Threads, has been…
Dec 17, 2024Ravie LakshmananMalware / Credential Theft A new social engineering campaign has leveraged Microsoft Teams as a way to…
Dec 17, 2024Ravie LakshmananCyber Attack / Malware A new phishing campaign has been observed employing tax-themed lures to deliver a…
Dec 17, 2024The Hacker NewsWebinar / Risk Management Even the best companies with the most advanced tools can still get…
Addressing cyber threats before they have a chance to strike or inflict serious damage is by far the best security…
Dec 17, 2024Ravie LakshmananCyber Espionage / Malware A suspected South Asian cyber espionage threat group known as Bitter targeted a…
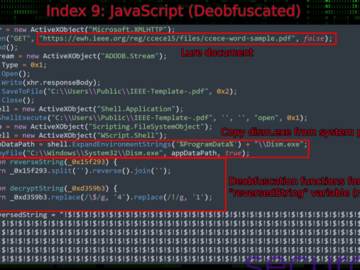
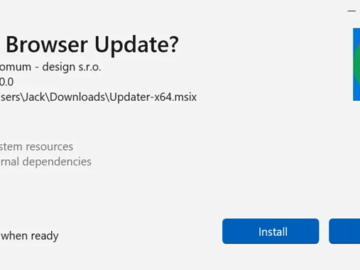
Bogus software update lures are being used by threat actors to deliver a new stealer malware called CoinLurker. “Written in…
Dec 17, 2024Ravie LakshmananNetwork Security / IoT Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two…