Category: TheHackerNews
Dec 17, 2024Ravie LakshmananCyber Espionage / Mobile Security A little-known cyber espionage actor known as The Mask has been linked…
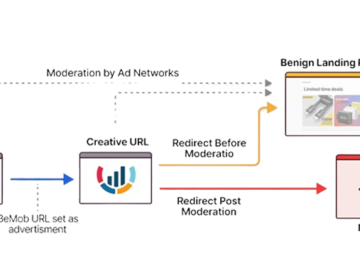
Dec 16, 2024Ravie LakshmananMalvertising / Threat Intelligence Cybersecurity researchers have shed light on a previously undocumented aspect associated with ClickFix-style…
Dec 16, 2024Ravie LakshmananSpyware / Surveillance A Serbian journalist had his phone first unlocked by a Cellebrite tool and subsequently…
With the evolution of modern software development, CI/CD pipeline governance has emerged as a critical factor in maintaining both agility…
Cybersecurity researchers have discovered a new PHP-based backdoor called Glutton that has been put to use in cyber attacks targeting…
Dec 16, 2024Ravie LakshmananCryptocurrency / Phishing Attack Cybersecurity researchers are calling attention to a new kind of investment scam that…
Dec 16, 2024Ravie LakshmananCyber Attack / Cyber Espionage The Security Service of Ukraine (SBU or SSU) has exposed a novel…
Dec 14, 2024Ravie LakshmananBotnet / Ad Fraud Germany’s Federal Office of Information Security (BSI) has announced that it has disrupted…
Dec 14, 2024Ravie LakshmananMalware / Cyber Threat Thai government officials have emerged as the target of a new campaign that…
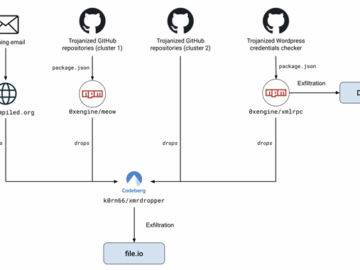
Dec 13, 2024Ravie LakshmananCyber Attack / Malware A now-removed GitHub repository that advertised a WordPress tool to publish posts to…
Dec 13, 2024The Hacker NewsLinux / Vulnerability A security flaw has been disclosed in OpenWrt’s Attended Sysupgrade (ASU) feature that,…
The U.S. Department of Justice (DoJ) has indicted 14 nationals belonging to the Democratic People’s Republic of Korea (DPRK or…