Category: TheHackerNews
Nov 28, 2024Ravie LakshmananWindows Security / Cryptomining A popular open-source game engine called Godot Engine is being misused as part…
Nov 28, 2024Ravie LakshmananNetwork Security / Cyber Espionage U.S. telecom service provider T-Mobile said it recently detected attempts made by…
Nov 27, 2024Ravie LakshmananVulnerability / Software Security A critical security flaw impacting the ProjectSend open-source file-sharing application has likely come…
Multi-stage cyber attacks, characterized by their complex execution chains, are designed to avoid detection and trick victims into a false…
Nov 27, 2024Ravie LakshmananLinux / Malware Cybersecurity researchers have shed light on what has been described as the first Unified…
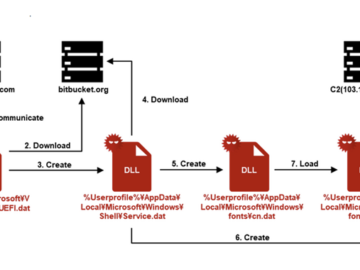
Nov 27, 2024Ravie LakshmananMalware / Cyber Espionage The threat actor known as APT-C-60 has been linked to a cyber attack…
Nov 27, 2024Ravie LakshmananCybercrime / Financial Fraud An INTERPOL-led operation has led to the arrest of 1,006 suspects across 19…
Nov 27, 2024Ravie LakshmananIoT Security / Network Security A threat actor named Matrix has been linked to a widespread distributed…
Nov 26, 2024Ravie LakshmananVulnerability / Website Security Two critical security flaws impacting the Spam protection, Anti-Spam, and FireWall plugin WordPress…
The China-linked threat actor known as Earth Estries has been observed using a previously undocumented backdoor called GHOSTSPIDER as part…
Nov 26, 2024The Hacker NewsPentest / Vulnerability Assessment When CVEs go viral, separating critical vulnerabilities from the noise is essential…
Nov 26, 2024Ravie LakshmananVulnerability / Cybercrime The Russia-aligned threat actor known as RomCom has been linked to the zero-day exploitation…