Category: TheHackerNews
Nov 26, 2024Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a now-patched…
Nov 25, 2024Ravie LakshmananSoftware Supply Chain / Malware The administrators of the Python Package Index (PyPI) repository have quarantined the…
Nov 25, 2024Ravie LakshmananMobile Security / Privacy Google has introduced a new feature called Restore Credentials to help users restore…
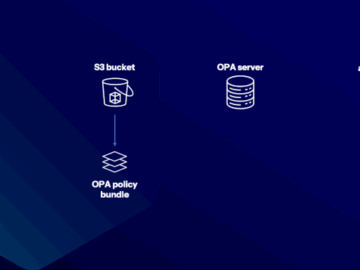
Nov 25, 2024Ravie LakshmananCloud Security / Supply Chain Attack Cybersecurity researchers have disclosed two new attack techniques against infrastructure-as-code (IaC)…
Dive into the evolution of phishing and malware evasion techniques and understand how attackers are using increasingly sophisticated methods to…
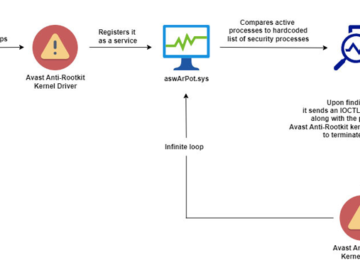
Nov 25, 2024Ravie LakshmananMalware / Windows Security Cybersecurity researchers have uncovered a new malicious campaign that leverages a technique called…
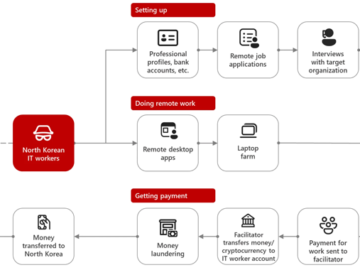
Nov 23, 2024Ravie LakshmananArtificial Intelligence / Cryptocurrency The North Korea-linked threat actor known as Sapphire Sleet is estimated to have…
Nov 23, 2024Ravie LakshmananCloud Security / Threat Intelligence Government agencies and non-governmental organizations in the United States have become the…
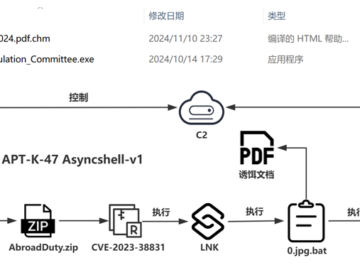
Nov 22, 2024Ravie LakshmananCyber Espionage / Malware A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in…
Nov 22, 2024Ravie LakshmananCyber Attack / Malware The threat actor known as Mysterious Elephant has been observed using an advanced…
Google Workspace has quickly become the productivity backbone for businesses worldwide, offering an all-in-one suite with email, cloud storage and…
Nov 22, 2024Ravie LakshmananCyber Espionage / Malware Threat actors with ties to Russia have been linked to a cyber espionage…