Category: TheHackerNews
U.S. telecoms giant T-Mobile has confirmed that it was also among the companies that were targeted by Chinese threat actors…
Nov 19, 2024Ravie LakshmananVulnerability / Data Security Now-patched security flaws impacting Progress Kemp LoadMaster and VMware vCenter Server have come…
According to research from GitGuardian and CyberArk, 79% of IT decision-makers reported having experienced a secrets leak, up from 75%…
Nov 18, 2024Ravie LakshmananThreat Intelligence / Ransomware Cybersecurity researchers have shed light on a new stealthy malware loader called BabbleLoader…
According to research from GitGuardian and CyberArk, 79% of IT decision-makers reported having experienced a secrets leak, up from 75%…
A new phishing campaign is targeting e-commerce shoppers in Europe and the United States with bogus pages that mimic legitimate…
Nov 18, 2024Ravie LakshmananMobile Security / Spyware Legal documents released as part of an ongoing legal tussle between Meta’s WhatsApp…
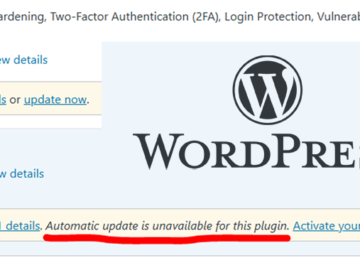
Nov 18, 2024Ravie LakshmananVulnerability / Website Security A critical authentication bypass vulnerability has been disclosed in the Really Simple Security…
Nov 16, 2024Ravie LakshmananVulnerability / Network Security Palo Alto Networks has released new indicators of compromise (IoCs) a day after…
A threat actor known as BrazenBamboo has exploited an unresolved security flaw in Fortinet’s FortiClient for Windows to extract VPN…
Nov 15, 2024Ravie LakshmananCyber Espionage / Malware Cybersecurity researchers have shed light on a new remote access trojan and information…
Nov 15, 2024The Hacker NewsWebinar / Cyber Security In the fast-paced digital world, trust is everything—but what happens when that…