Category: TheHackerNews
Dec 07, 2024Ravie LakshmananSupply Chain Attack / Cryptocurrency In yet another software supply chain attack, it has come to light…
Dec 06, 2024Ravie LakshmananSpyware / Mobile Security A Russian programmer accused of donating money to Ukraine had his Android device…
The modern business landscape is thrilling yet daunting. Rapidly evolving technology, persistent cyberthreats and escalating operational complexities make data protection…
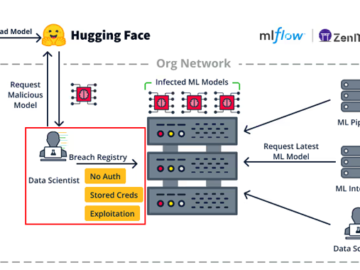
Dec 06, 2024Ravie LakshmananArtificial Intelligence / Vulnerability Cybersecurity researchers have disclosed multiple security flaws impacting open-source machine learning (ML) tools…
Dec 06, 2024Ravie LakshmananMalware / Cybercrime The threat actors behind the More_eggs malware have been linked to two new malware…
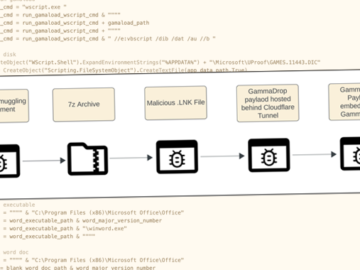
Dec 06, 2024The Hacker NewsMalware / Threat Intelligence The threat actor known as Gamaredon has been observed leveraging Cloudflare Tunnels…
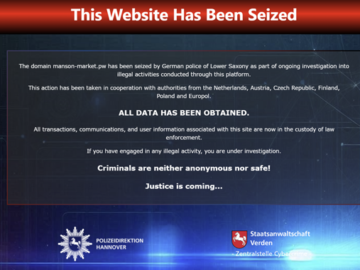
Dec 05, 2024Ravie LakshmananOnline Fraud / Cybercrime Europol on Thursday announced the shutdown of a clearnet marketplace called Manson Market…
Dec 05, 2024Ravie LakshmananCryptocurrency / Mobile Security As many as 77 banking institutions, cryptocurrency exchanges, and national organizations have become…
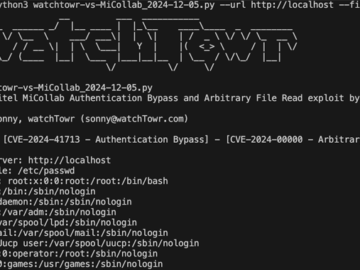
Dec 05, 2024Ravie LakshmananVulnerability / IoT Security Cybersecurity researchers have released a proof-of-concept (PoC) exploit that strings together a now-patched…
A previously undocumented threat activity cluster dubbed Earth Minotaur is leveraging the MOONSHINE exploit kit and an unreported Android-cum-Windows backdoor…
Vulnerability Management (VM) has long been a cornerstone of organizational cybersecurity. Nearly as old as the discipline of cybersecurity itself,…
Dec 05, 2024Ravie LakshmananThreat Intelligence / Cyber Espionage A suspected Chinese threat actor targeted a large U.S. organization earlier this…