Category: TheHackerNews
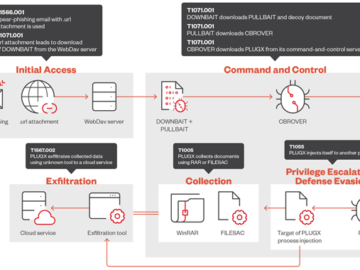
Sep 10, 2024Ravie LakshmananMalware / Cyber Espionage A trio of threat activity clusters linked to China has been observed compromising…
Shadow apps, a segment of Shadow IT, are SaaS applications purchased without the knowledge of the security team. While these…
Sep 10, 2024Ravie LakshmananCyber Attack / Malware The threat actor tracked as Mustang Panda has refined its malware arsenal to…
Sep 09, 2024Ravie LakshmananCyber Espionage / Malware The China-linked advanced persistent threat (APT) group known as Mustang Panda has been…
Sep 09, 2024Ravie LakshmananFinancial Security / Malware The Colombian insurance sector is the target of a threat actor tracked as…
Sep 09, 2024Ravie LakshmananVulnerability / Hardware Security A novel side-channel attack has been found to leverage radio signals emanated by…
Sep 09, 2024The Hacker NewsData Protection / Threat Detection The proliferation of cybersecurity tools has created an illusion of security….
Sep 09, 2024The Hacker NewsData Security / GenAI Security GenAI has become a table stakes tool for employees, due to…
Sep 09, 2024Ravie LakshmananVulnerability / Enterprise Security Progress Software has released security updates for a maximum-severity flaw in LoadMaster and…
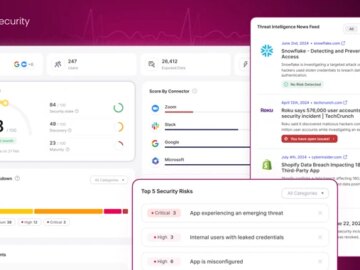
Sep 09, 2024The Hacker NewsSaaS Security / Risk Management Designed to be more than a one-time assessment— Wing Security’s SaaS…
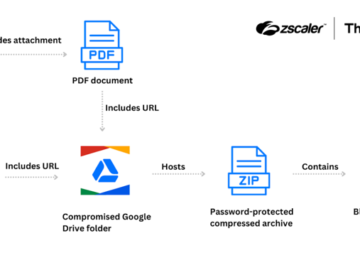
Sep 09, 2024Ravie LakshmananCyber Attack / Threat Intelligence A previously undocumented threat actor with likely ties to Chinese-speaking groups has…
Sep 09, 2024Ravie LakshmananMobile Security / Cryptocurrency Android device users in South Korea have emerged as a target of a…