Category: TheHackerNews
Sep 05, 2024Ravie LakshmananThreat Prevention / Software Security Veeam has shipped security updates to address a total of 18 security…
Sep 05, 2024Ravie LakshmananMalware / Human Rights Unnamed government entities in the Middle East and Malaysia are the target of…
The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 32 internet domains used by a pro-Russian propaganda…
Sep 05, 2024The Hacker NewsThreat Detection / Vulnerability Management It’s been a decade since the National Institute of Standards and…
Sep 05, 2024Ravie LakshmananCyber Threat / Malware Threat actors are likely employing a tool designated for red teaming exercises to…
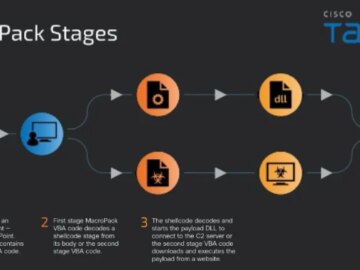
Sep 05, 2024Ravie LakshmananCyber Attack / Malware The Chinese-speaking threat actor known as Earth Lusca has been observed using a…
Sep 05, 2024Ravie Lakshmanan Cisco has released security updates for two critical security flaws impacting its Smart Licensing Utility that…
North Korean threat actors have leveraged a fake Windows video conferencing application impersonating FreeConference.com to backdoor developer systems as part…
Sep 04, 2024Ravie LakshmananVulnerability / Mobile Security Google has released its monthly security updates for the Android operating system to…
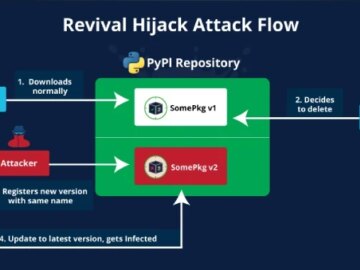
Sep 04, 2024Ravie Lakshmanan A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited…
Sep 04, 2024Ravie LakshmananVulnerability / Network Security Zyxel has released software updates to address a critical security flaw impacting certain…
Sep 04, 2024The Hacker NewsSaaS Security / Browser Security Account takeover attacks have emerged as one of the most persistent…