Category: TheHackerNews
Aug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers…
Aug 30, 2024Ravie LakshmananCryptojacking / Vulnerability Threat actors are actively exploiting a now-patched, critical security flaw impacting the Atlassian Confluence…
Aug 30, 2024Ravie LakshmananMalware / Network Security Cybersecurity researchers have disclosed a new campaign that potentially targets users in the…
Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. The activity, detected…
The most dangerous vulnerability you’ve never heard of. In the world of cybersecurity, vulnerabilities are discovered so often, and at…
Aug 30, 2024Ravie LakshmananCyber Threat / Cyber Espionage Cybersecurity researchers have unearthed new network infrastructure set up by Iranian threat…
Aug 30, 2024Ravie LakshmananCyber Espionage / Threat Intelligence Chinese-speaking users are the target of a “highly organized and sophisticated attack”…
Aug 30, 2024The Hacker NewsICS Security / OT Security A comprehensive guide authored by Dean Parsons emphasizes the growing need…
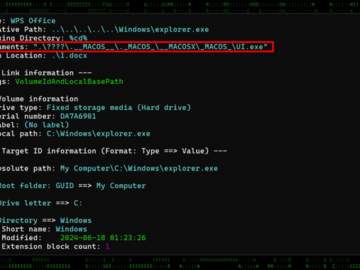
Aug 30, 2024Ravie LakshmananCryptocurrency / Malware Threat actors with ties to North Korea have been observed publishing a set of…
Aug 29, 2024Ravie LakshmananBrowser Security / Vulnerability Cybersecurity researchers have flagged multiple in-the-wild exploit campaigns that leveraged now-patched flaws in…
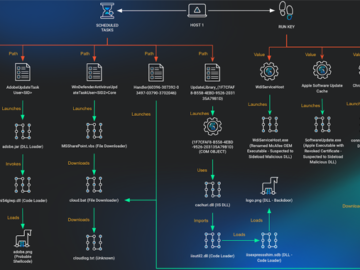
Aug 29, 2024Ravie LakshmananCyber Espionage / Malware A non-profit supporting Vietnamese human rights has been the target of a multi-year…
Aug 29, 2024Ravie LakshmananIoT Security / Vulnerability A years-old high-severity flaw impacting AVTECH IP cameras has been weaponized by malicious…