Category: TheHackerNews
Aug 27, 2024Ravie LakshmananVulnerability / Browser Security Google has revealed that a security flaw that was patched as part of…
Aug 27, 2024Ravie LakshmananAI Security / Vulnerability Details have emerged about a now-patched vulnerability in Microsoft 365 Copilot that could…
Aug 26, 2024Ravie LakshmananGDPR / Data Protection The Dutch Data Protection Authority (DPA) has fined Uber a record €290 million…
Aug 26, 2024Ravie LakshmananVulnerability / Enterprise Security SonicWall has released security updates to address a critical flaw impacting its firewalls…
Aug 26, 2024The Hacker NewsData Security / Compliance Nowadays, sensitive and critical data is traveling in everyday business channels that…
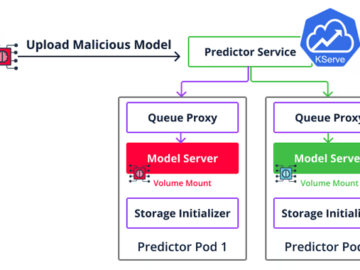
Cybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of…
Aug 26, 2024Ravie LakshmananSoftware Security / Vulnerability Two security vulnerabilities have been disclosed in the open-source Traccar GPS tracking system…
Aug 26, 2024Ravie LakshmananFinancial Fraud / Mobile Security Cybersecurity researchers have uncovered new Android malware that can relay victims’ contactless…
Aug 25, 2024Ravie LakshmananFinancial Fraud / Cybercrime Cybersecurity researchers have uncovered a new stealthy piece of Linux malware that leverages…
Aug 25, 2024Ravie LakshmananLaw Enforcement / Digital Privacy Pavel Durov, founder and chief executive of the popular messaging app Telegram,…
Aug 24, 2024Ravie LakshmananElection Security / Threat Intelligence Meta Platforms on Friday became the latest company after Microsoft, Google, and…
Aug 24, 2024Ravie LakshmananVulnerability / Government Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has placed a security flaw…