Category: TheHackerNews
Aug 20, 2024Ravie LakshmananVulnerability / Container Security Cybersecurity researchers have disclosed a security flaw impacting Microsoft Azure Kubernetes Services that,…
Aug 20, 2024Ravie LakshmananVulnerability / Threat Intelligence A previously undocumented backdoor named Msupedge has been put to use against a…
Aug 20, 2024Ravie LakshmananVulnerability / Ransomware The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw…
Aug 20, 2024Ravie LakshmananMalware / Cyber Espionage Cybersecurity researchers have shed light on a threat actor known as Blind Eagle…
Aug 20, 2024Ravie LakshmananEnterprise Security / Data Breach Cybersecurity researchers are warning about the discovery of thousands of externally-facing Oracle…
Aug 19, 2024Ravie LakshmananMalvertising / Cybercrime Cybersecurity researchers have uncovered a surge in malware infections stemming from malvertising campaigns distributing…
Aug 19, 2024Ravie LakshmananThreat Intelligence / Cryptocurrency A new type of malware called UULoader is being used by threat actors…
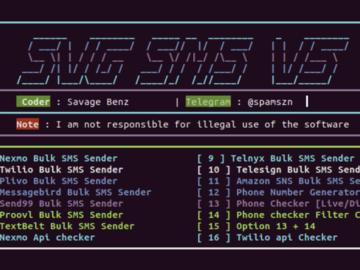
Aug 19, 2024Ravie LakshmananCloud Security / Threat Intelligence Malicious actors are using a cloud attack tool named Xeon Sender to…
Aug 19, 2024Ravie LakshmananVulnerability / Zero-Day A newly patched security flaw in Microsoft Windows was exploited as a zero-day by…
Aug 19, 2024Ravie LakshmananCybercrime / Network Security Cybersecurity researchers have discovered new infrastructure linked to a financially motivated threat actor…
OpenAI on Friday said it banned a set of accounts linked to what it said was an Iranian covert influence…
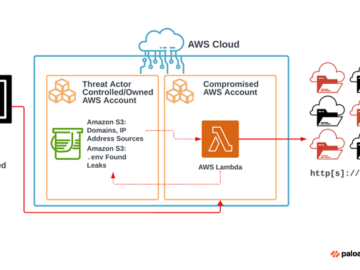
Aug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of…