Category: TheHackerNews
Aug 07, 2024Ravie LakshmananEmail Security / Vulnerability Cybersecurity researchers have disclosed details of security flaws in the Roundcube webmail software…
Aug 07, 2024Ravie LakshmananLinux / Vulnerability Cybersecurity researchers have shed light on a novel Linux kernel exploitation technique dubbed SLUBStick…
Aug 07, 2024Ravie LakshmananCybersecurity / Incident Response Cybersecurity company CrowdStrike has published its root cause analysis detailing the Falcon Sensor…
Aug 07, 2024Ravie LakshmananCloud Security / Cyber Espionage An unnamed media organization in South Asia was targeted in November 20233…
Aug 07, 2024Ravie LakshmananAndroid / Mobile Security, Cybersecurity researchers have lifted the lid on a new technique adopted by threat…
Aug 07, 2024Ravie LakshmananMalware / Software Security Apple on Tuesday announced an update to its next-generation macOS version that makes…
Aug 06, 2024Ravie LakshmananEmail Security / Financial Fraud INTERPOL said it devised a “global stop-payment mechanism” that helped facilitate the…
Aug 06, 2024The Hacker NewsSaaS Security / Threat Detection Everyone loves the double-agent plot twist in a spy movie, but…
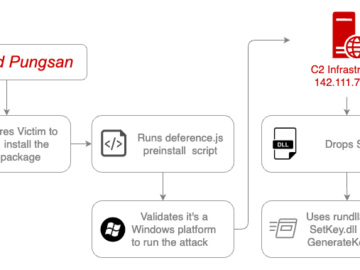
Aug 06, 2024Ravie LakshmananMalware / Windows Security The North Korea-linked threat actor known as Moonstone Sleet has continued to push…
Aug 06, 2024Ravie LakshmananAndroid / Malware Users in Russia have been the target of a previously undocumented Android post-compromise spyware…
Aug 06, 2024Ravie LakshmananMobile Security / Vulnerability Google has addressed a high-severity security flaw impacting the Android kernel that it…
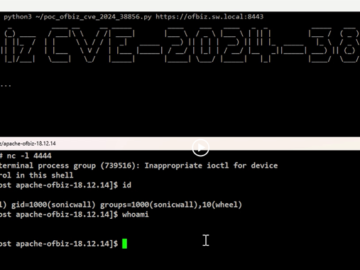
Aug 06, 2024Ravie LakshmananEnterprise Security / Vulnerability A new zero-day pre-authentication remote code execution vulnerability has been disclosed in the…