Category: TheHackerNews
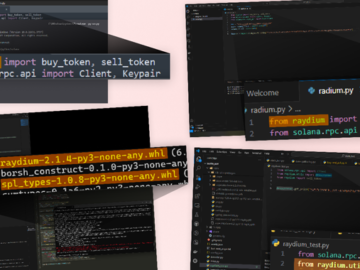
Jul 31, 2024Ravie LakshmananMalware / Software Development The threat actors behind an ongoing malware campaign targeting software developers have demonstrated…
We’ll TL;DR the FUDdy introduction: we all know that phishing attacks are on the rise in scale and complexity, that…
Jul 31, 2024Ravie LakshmananCyber Attack / Threat Intelligence Japanese organizations are the target of a Chinese nation-state threat actor that…
Jul 31, 2024Ravie LakshmananMobile Security / Malware A new malicious campaign has been observed making use of malicious Android apps…
Jul 31, 2024Ravie LakshmananPrivacy / Social Media Meta, the parent company of Facebook, Instagram, and WhatsApp, agreed to a record…
Jul 30, 2024The Hacker NewsDark Web Intelligence Learn about critical threats that can impact your organization and the bad actors…
As more people work remotely, IT departments must manage devices distributed over different cities and countries relying on VPNs and…
Jul 30, 2024Ravie LakshmananMobile Security / Spyware A new iteration of a sophisticated Android spyware called Mandrake has been discovered…
Jul 30, 2024Ravie LakshmananMalware / Cyber Threat Cybersecurity researchers have detailed widespread phishing campaigns targeting small and medium-sized businesses (SMBs)…
Jul 30, 2024Ravie LakshmananCyber Espionage / Malware The nation-state threat actor known as SideWinder has been attributed to a new…
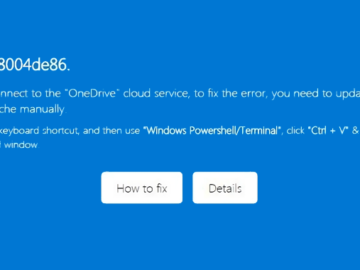
Jul 30, 2024Ravie LakshmananMalware / Email Security Cybersecurity researchers are warning about a new phishing campaign that targets Microsoft OneDrive…
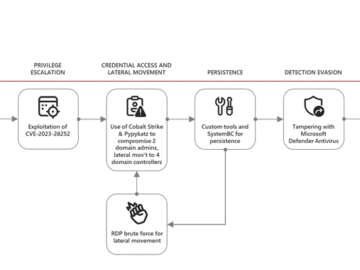
A recently patched security flaw impacting VMware ESXi hypervisors has been actively exploited by “several” ransomware groups to gain elevated…