Category: TheHackerNews
Jul 29, 2024Ravie LakshmananEnterprise Security / Data Protection Cybersecurity company Acronis is warning that a now-patched critical security flaw impacting…
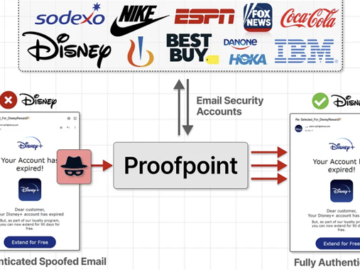
An unknown threat actor has been linked to a massive scam campaign that exploited an email routing misconfiguration in email…
Searchable Encryption has long been a mystery. An oxymoron. An unattainable dream of cybersecurity professionals everywhere. Organizations know they must…
A threat actor known as Stargazer Goblin has set up a network of inauthentic GitHub accounts to fuel a Distribution-as-a-Service…
Jul 29, 2024NewsroomCybersecurity / Cyber Espionage The remote access trojan known as Gh0st RAT has been observed being delivered by…
Jul 27, 2024NewsroomMalware / Cyber Intelligence French judicial authorities, in collaboration with Europol, have launched a so-called “disinfection operation” to…
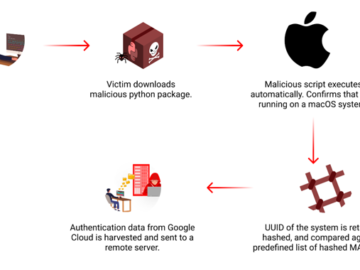
Jul 27, 2024NewsroomCybersecurity / Cloud Security Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository…
A Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS)…
Jul 26, 2024The Hacker NewsDigital Warfare / Cybersecurity Training “Peace is the virtue of civilization. War is its crime. Yet…
The U.S. Department of Justice (DoJ) on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly…
Jul 26, 2024Mohit KumarEnterprise Security / Network Security CrowdStrike is alerting about an unfamiliar threat actor attempting to capitalize on…
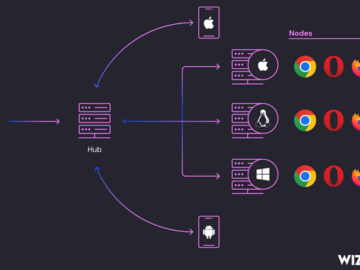
Jul 26, 2024Newsroom Cybersecurity researchers are sounding the alarm over an ongoing campaign that’s leveraging internet-exposed Selenium Grid services for…