Category: TheHackerNews
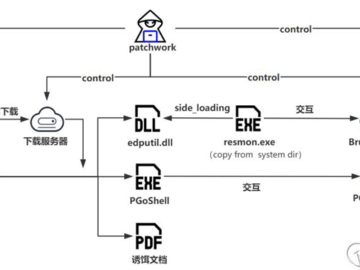
Jul 24, 2024NewsroomCyber Espionage / Threat Intelligence The threat actor known as Patchwork has been linked to a cyber attack…
Jul 24, 2024The Hacker NewsSaaS Management / IT Governance There is one simple driver behind the modern explosion in SaaS…
Jul 24, 2024NewsroomSoftware Update / IT Outage Cybersecurity firm CrowdStrike on Wednesday blamed an issue in its validation system for…
Jul 24, 2024NewsroomVulnerability / Software Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to…
Jul 24, 2024NewsroomMalvertising / Threat Intelligence A now-patched security flaw in the Microsoft Defender SmartScreen has been exploited as part…
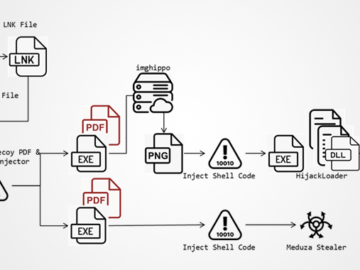
Jul 23, 2024NewsroomCyber Espionage / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has alerted of a spear-phishing campaign…
Jul 23, 2024NewsroomCyber Espionage / Chinese Hackers Organizations in Taiwan and a U.S. non-governmental organization (NGO) based in China have…
Meta has been given time till September 1, 2024, to respond to concerns raised by the European Commission over its…
Jul 23, 2024NewsroomICS Malware / Critical Infrastructure Cybersecurity researchers have discovered what they say is the ninth Industrial Control Systems…
Jul 23, 2024NewsroomThreat Detection / Website Security Threat actors have been observed using swap files in compromised websites to conceal…
Jul 23, 2024The Hacker NewsCorporate Security / Data Protection The initial onboarding stage is a crucial step for both employees…
Jul 23, 2024NewsroomOnline Privacy / Regulatory Compliance Google on Monday abandoned plans to phase out third-party tracking cookies in its…