Category: TheHackerNews
As a vCISO, you are responsible for your client’s cybersecurity strategy and risk governance. This incorporates multiple disciplines, from research…
The opportunities to use AI in workflow automation are many and varied, but one of the simplest ways to use…
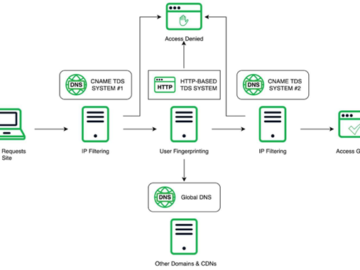
The relationship between various TDSs and DNS associated with Vigorish Viper and the final landing experience for the user A…
Jul 22, 2024NewsroomCloud Security / Phishing Attack A Latin America (LATAM)-based financially motivated actor codenamed FLUXROOT has been observed leveraging…
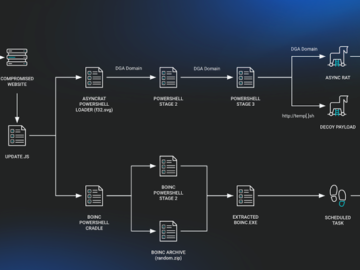
Jul 22, 2024NewsroomVulnerability / Malware The JavaScript downloader malware known as SocGholish (aka FakeUpdates) is being used to deliver a…
Cybersecurity researchers have discovered a new Linux variant of a ransomware strain known as Play (aka Balloonfly and PlayCrypt) that’s…
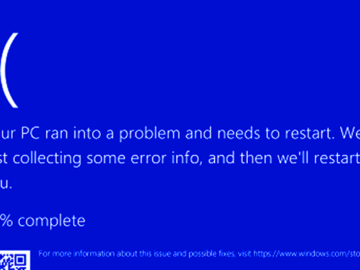
Jul 20, 2024NewsroomMalware / IT Outage Cybersecurity firm CrowdStrike, which is facing the heat for causing worldwide IT disruptions by…
Jul 20, 2024NewsroomCybercrime / Data Breach Law enforcement officials in the U.K. have arrested a 17-year-old boy from Walsall who…
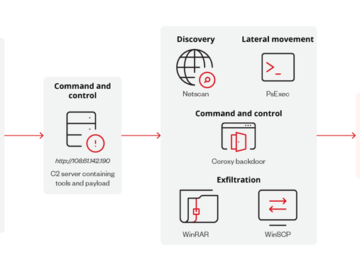
Jul 19, 2024NewsroomRansomware / Cybercrime Two Russian nationals have pleaded guilty in a U.S. court for their participation as affiliates…
Businesses across the world have been hit by widespread disruptions to their Windows workstations stemming from a faulty update pushed…
Jul 19, 2024NewsroomVulnerability / Enterprise Security SolarWinds has addressed a set of critical security flaws impacting its Access Rights Manager…
Learn about critical threats that can impact your organization and the bad actors behind them from Cybersixgill’s threat experts. Each…