Category: TheHackerNews
Jul 19, 2024The Hacker NewsMalware / Mobile Security A suspected pro-Houthi threat group targeted at least three humanitarian organizations in…
Jul 19, 2024NewsroomCyber Espionage / Threat Intelligence Several organizations operating within global shipping and logistics, media and entertainment, technology, and…
Jul 19, 2024The Hacker NewsTechnology / Artificial Intelligence Event Overview The “AI Leaders Spill Their Secrets” webinar, hosted by Sigma…
Jul 19, 2024NewsroomCryptocurrency / Cybercrime Indian cryptocurrency exchange WazirX has confirmed that it was the target of a security breach…
Jul 18, 2024NewsroomOpen-Source / Cybercrime Unknown threat actors have been observed leveraging open-source tools as part of a suspected cyber…
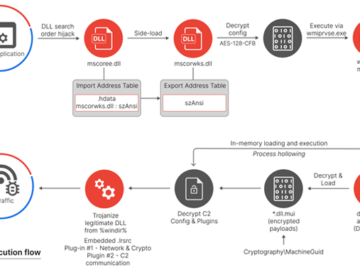
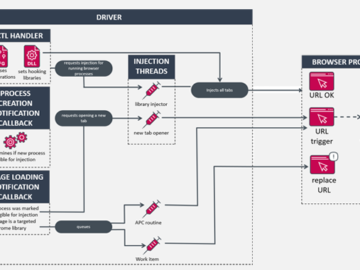
Jul 18, 2024NewsroomMalware / Windows Security Cybersecurity researchers have shed light on an adware module that purports to block ads…
Jul 18, 2024The Hacker NewsApp Security / Security Awareness Let’s face it: AppSec and developers often feel like they’re on…
Jul 18, 2024The Hacker NewsCybersecurity / Bot Attacks As the travel industry rebounds post-pandemic, it is increasingly targeted by automated…
Jul 18, 2024NewsroomCloud Security / Enterprise Security Cybersecurity researchers have uncovered security shortcomings in SAP AI Core cloud-based platform for…
Jul 18, 2024NewsroomArtificial Intelligence / Data Protection Meta has suspended the use of generative artificial intelligence (GenAI) in Brazil after…
Jul 18, 2024Newsroom Cisco has released patches to address a maximum-severity security flaw impacting Smart Software Manager On-Prem (Cisco SSM…
Jul 17, 2024NewsroomCyber Espionage / Cryptocurrency Cybersecurity researchers have discovered an updated variant of a known stealer malware that attackers…