Category: TheHackerNews
Jul 08, 2024NewsroomDark Web / Cyber Crime An analysis of information-stealing malware logs published on the dark web has led…
Jul 08, 2024NewsroomRansomware / Encryption An emerging ransomware-as-a-service (RaaS) operation called Eldorado comes with locker variants to encrypt files on…
Jul 08, 2024The Hacker NewsCybersecurity / Enterprise Security Events like the recent massive CDK ransomware attack – which shuttered car…
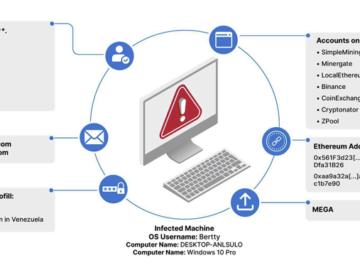
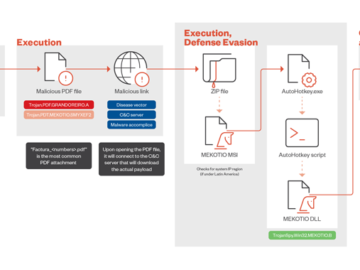
Jul 08, 2024NewsroomMalware / Cyber Threat Financial institutions in Latin America are being threatened by a banking trojan called Mekotio…
Jul 08, 2024NewsroomVulnerability / Software Security Four unpatched security flaws, including three critical ones, have been disclosed in the Gogs…
Jul 08, 2024NewsroomPrivacy / Internet Censorship Apple removed a number of virtual private network (VPN) apps in Russia from its…
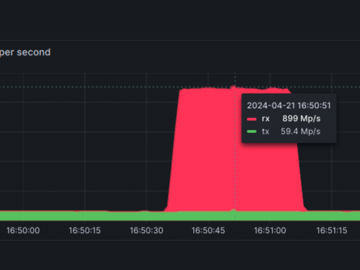
Jul 05, 2024NewsroomNetwork Security / DDoS Attack French cloud computing firm OVHcloud said it mitigated a record-breaking distributed denial-of-service (DDoS)…
Jul 05, 2024The Hacker NewsCybersecurity / Identity Protection Identity theft isn’t just about stolen credit cards anymore. Today, cybercriminals are…
Jul 05, 2024The Hacker NewsCloud Security / Attack Surface The attack surface isn’t what it once was and it’s becoming…
Jul 05, 2024NewsroomSEO Poisoning / Cyber Attack, The malware known as GootLoader continues to be in active use by threat…
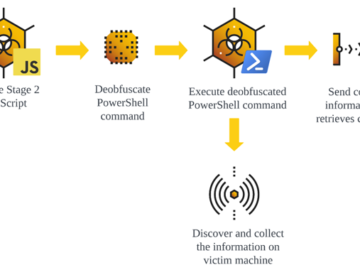
Jul 05, 2024NewsroomSupply Chain Attack / Malware The supply chain attack targeting widely-used Polyfill[.]io JavaScript library is wider in scope…
Jul 05, 2024NewsroomNetwork Security / Cyber Attack Cybersecurity researchers have uncovered a new botnet called Zergeca that’s capable of conducting…




![Polyfill[.]io Attack Impacts Over 380,000 Hosts, Including Major Companies Polyfill Attack](https://image.cybernoz.com/wp-content/uploads/2024/07/Polyfillio-Attack-Impacts-Over-380000-Hosts-Including-Major-Companies-360x270.png)
