Category: TheHackerNews
Jul 04, 2024NewsroomVulnerability / Critical Infrastructure Microsoft has revealed two security flaws in Rockwell Automation PanelView Plus that could be…
Jul 04, 2024NewsroomArtificial Intelligence / Data Privacy Brazil’s data protection authority, Autoridade Nacional de Proteção de Dados (ANPD), has temporarily…
A coordinated law enforcement operation codenamed MORPHEUS has felled close to 600 servers that were used by cybercriminal groups and…
Jul 04, 2024NewsroomData Breach / Mobile Security Cloud communications provider Twilio has revealed that unidentified threat actors took advantage of…
Jul 03, 2024The Hacker NewsOSINT / Artificial Intelligence Recently the Office of the Director of National Intelligence (ODNI) unveiled a…
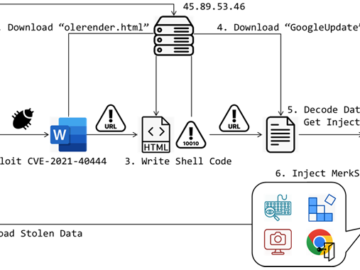
Jul 03, 2024NewsroomSpyware / Vulnerability Unknown threat actors have been observed exploiting a now-patched security flaw in Microsoft MSHTML to…
Jul 03, 2024NewsroomMalware / SEO Poisoning The loader-as-a-service (LaaS) known as FakeBat has become one of the most widespread loader…
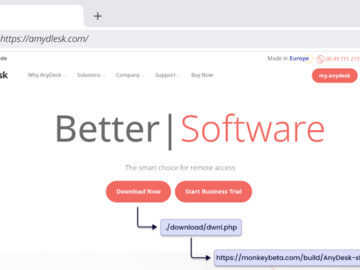
Jul 03, 2024NewsroomMalware / Threat Intelligence An unnamed South Korean enterprise resource planning (ERP) vendor’s product update server has been…
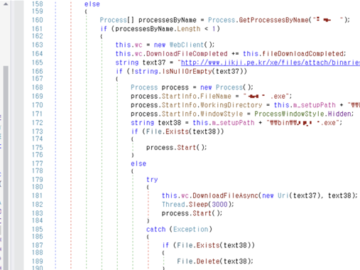
Jul 03, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered an attack campaign that targets various Israeli entities with publicly-available…
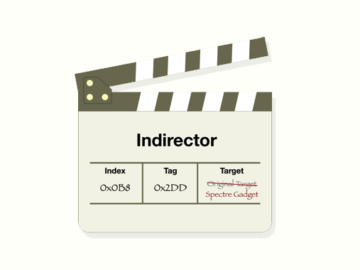
Jul 02, 2024NewsroomHardware Security / Vulnerability Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable…
The cybersecurity threat landscape has witnessed a dramatic and alarming rise in the average ransomware payment, an increase exceeding 500%….
Jul 02, 2024NewsroomCyber Espionage / Vulnerability A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day…