Category: TheHackerNews
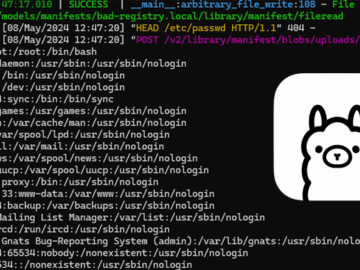
Jun 24, 2024NewsroomArtificial Intelligence / Cloud Security Cybersecurity researchers have detailed a now-patch security flaw affecting the Ollama open-source artificial…
Jun 24, 2024The Hacker NewsThreat Intelligence / Cybersecurity Learn about critical threats that can impact your organization and the bad…
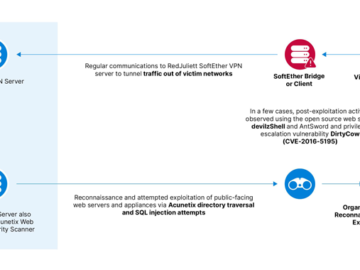
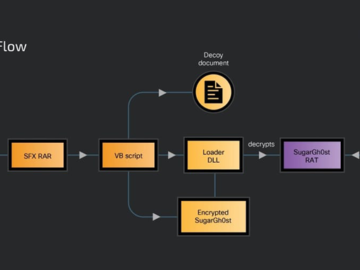
Jun 24, 2024NewsroomCyber Espionage / Hacking A likely China-linked state-sponsored threat actor has been linked to a cyber espionage campaign…
Jun 24, 2024NewsroomMobile Security / Threat Intelligence Multiple threat actors, including cyber espionage groups, are employing an open-source Android remote…
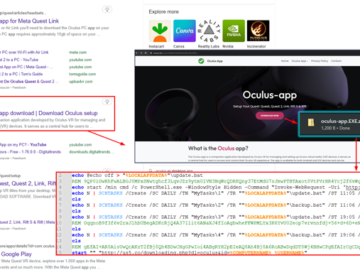
Jun 22, 2024NewsroomPhishing Attack / Adware A new campaign is tricking users searching for the Meta Quest (formerly Oculus) application…
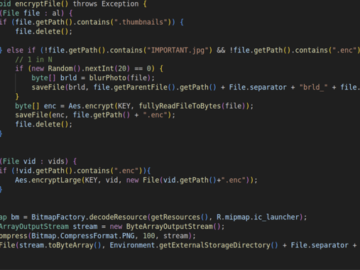
Jun 22, 2024NewsroomCyber Espionage / Threat Intelligence Russian organizations have been targeted by a cybercrime gang called ExCobalt using a…
Jun 22, 2024NewsroomNational Security / Cyber Espionage The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed…
Jun 21, 2024NewsroomMalware / Threat Intelligence A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage…
Jun 21, 2024NewsroomPhishing Attack / Email Security Cybersecurity researchers have shed light on a new phishing campaign that has been…
Jun 21, 2024NewsroomMalware / Malvertising A malvertising campaign is leveraging trojanized installers for popular software such as Google Chrome and…
Jun 21, 2024NewsroomVulnerability / Data Protection A recently patched high-severity flaw impacting SolarWinds Serv-U file transfer software is being actively…
Jun 21, 2024NewsroomSoftware Security / Threat Intelligence The U.S. Department of Commerce’s Bureau of Industry and Security (BIS) on Thursday…