Category: TheHackerNews
Jun 16, 2024NewsroomCybercrime / SIM Swapping Law enforcement authorities have allegedly arrested a key member of the notorious cybercrime group…
Jun 15, 2024Newsroom Pakistan has become the latest target of a threat actor called the Smishing Triad, marking the first…
Jun 15, 2024NewsroomArtificial Intelligence / Privacy Meta on Friday said it’s delaying its efforts to train the company’s large language…
Jun 14, 2024NewsroomPrivacy / Ad Tracking Google’s plans to deprecate third-party tracking cookies in its Chrome web browser with Privacy…
Jun 14, 2024The Hacker News Data is growing faster than ever. Remember when petabytes (that’s 1,000,000 gigabytes!) were only for…
Jun 14, 2024The Hacker NewsCybersecurity / Regulatory Compliance As cyber threats loom large and data breaches continue to pose increasingly…
Jun 14, 2024NewsroomDevice Security / Authentication An analysis of a hybrid biometric access system from Chinese manufacturer ZKTeco has uncovered…
Threat actors linked to North Korea have accounted for one-third of all the phishing activity targeting Brazil since 2020, as…
Jun 14, 2024NewsroomArtificial Intelligence / Data Protection Microsoft on Thursday revealed that it’s delaying the rollout of the controversial artificial…
Jun 13, 2024NewsroomThreat Intelligence / Mobile Security The threat actor known as Arid Viper has been attributed to a mobile…
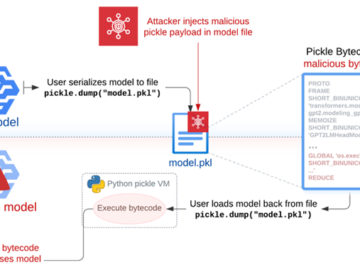
Jun 13, 2024NewsroomVulnerability / Software Security The security risks posed by the Pickle format have once again come to the…
Jun 13, 2024NewsroomSaaS Security / Shadow IT Recent supply chain cyber-attacks are prompting cyber security regulations in the financial sector…