Category: TheHackerNews
Jun 06, 2024NewsroomSoftware Security / Data Theft Cybersecurity researchers have discovered a malicious Python package uploaded to the Python Package…
Early in 2024, Wing Security released its State of SaaS Security report, offering surprising insights into emerging threats and best…
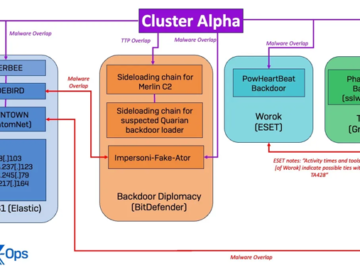
Jun 05, 2024NewsroomCyber Espionage / Threat Intelligence An unnamed high-profile government organization in Southeast Asia emerged as the target of…
An analysis of a nascent ransomware strain called RansomHub has revealed it to be an updated and rebranded version of…
Jun 05, 2024NewsroomVulnerability / Data Security Zyxel has released security updates to address critical flaws impacting two of its network-attached…
Jun 05, 2024NewsroomCyber Attack / Online Security Popular video-sharing platform TikTok has acknowledged a security issue that has been exploited…
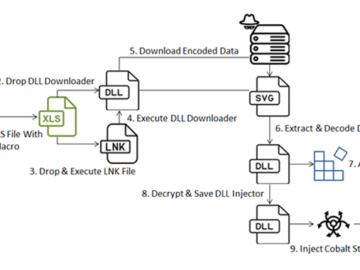
Jun 04, 2024NewsroomCyber Attack / Malware Russian organizations are at the receiving end of cyber attacks that have been found…
Jun 04, 2024NewsroomServer Security / Vulnerability Progress Software has rolled out updates to address a critical security flaw impacting the…
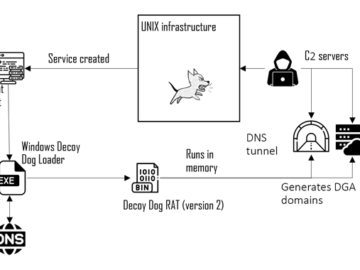
Jun 04, 2024NewsroomCyber Attack / Malware A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with…
Jun 04, 2024The Hacker NewsBrowser Security / Enterprise Security The landscape of browser security has undergone significant changes over the…
Jun 04, 2024NewsroomCloud Security / Data Protection Cloud computing and analytics company Snowflake said a “limited number” of its customers…
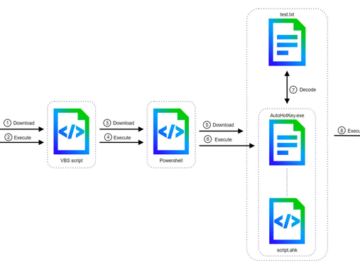
Jun 04, 2024NewsroomVulnerability / Threat Intelligence Cyber attacks involving the DarkGate malware-as-a-service (MaaS) operation have shifted away from AutoIt scripts…