Category: TheHackerNews
The financially motivated threat actor known as FIN7 has been observed leveraging malicious Google ads spoofing legitimate brands as a…
May 10, 2024NewsroomMalware / Cyber Espionage The North Korean threat actor tracked as Kimsuky has been observed deploying a previously…
May 10, 2024The Hacker NewsArtificial Intelligence / Threat Hunting Artificial intelligence (AI) is transforming cybersecurity, and those leading the charge…
Malicious Android apps masquerading as Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) have been observed to steal users’ credentials…
A guide to finding the right endpoint detection and response (EDR) solution for your business’ unique needs. Cybersecurity has become…
May 10, 2024NewsroomBrowser Security / Vulnerability Google on Thursday released security updates to address a zero-day flaw in Chrome that…
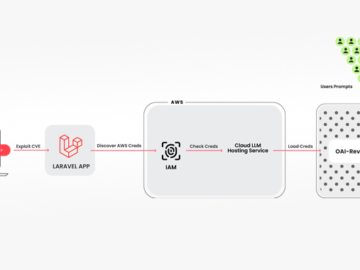
May 10, 2024NewsroomVulnerability / Cloud Security Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target…
May 09, 2024NewsroomEncryption / Data Privacy Researchers have detailed a Virtual Private Network (VPN) bypass technique dubbed TunnelVision that allows…
May 09, 2024NewsroomMobile Security / Cyber Attack Polish government institutions have been targeted as part of a large-scale malware campaign…
May 09, 2024NewsroomNetwork Security / Botnet Two recently disclosed security flaws in Ivanti Connect Secure (ICS) devices are being exploited…
May 09, 2024The Hacker NewsvCISO / Regulatory Compliance Cybersecurity and compliance guidance are in high demand among SMEs. However, many…
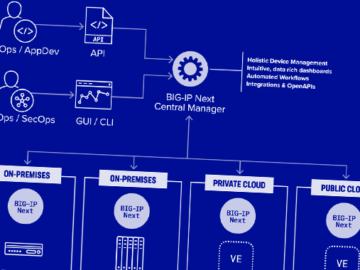
May 09, 2024NewsroomFirewall / Network Security Two security vulnerabilities have been discovered in F5 Next Central Manager that could be…