Category: TheHackerNews
May 02, 2024NewsroomVulnerability / Android Several popular Android applications available in Google Play Store are susceptible to a path traversal-affiliated…
May 02, 2024NewsroomRansomware / Cyber Crime A Ukrainian national has been sentenced to more than 13 years in prison and…
A never-before-seen botnet called Goldoon has been observed targeting D-Link routers with a nearly decade-old critical security flaw with the…
May 02, 2024NewsroomCyber Attack / Data Breach Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign)…
Like antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to give…
May 02, 2024NewsroomVulnerability / Data Breach The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting…
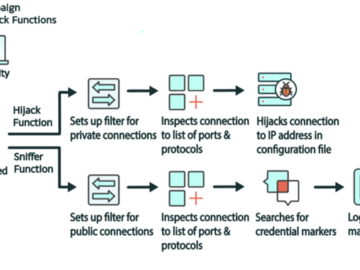
May 02, 2024NewsroomCyber Espionage / Network Security A new malware called Cuttlefish is targeting small office and home office (SOHO)…
May 01, 2024NewsroomFinancial Crime / Forensic Analysis A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain…
May 01, 2024NewsroomMalware / Android Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress…
May 01, 2024NewsroomMalware / Cyber Threat The authors behind the resurfaced ZLoader malware have added a feature that was originally…
May 01, 2024The Hacker NewsSecurity Awareness Training There’s a natural human desire to avoid threatening scenarios. The irony, of course,…
May 01, 2024NewsroomNational Security / Insider Threat A former employee of the U.S. National Security Agency (NSA) has been sentenced…