Category: TheHackerNews
Apr 24, 2024NewsroomEncryption / Mobile Security Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users’…
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus software to distribute backdoors and cryptocurrency…
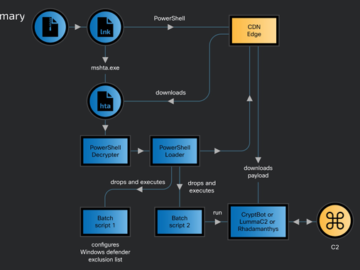
Apr 24, 2024NewsroomMalware / Data Security A new ongoing malware campaign has been observed distributing three different stealers, such as…
Apr 23, 2024NewsroomSupply Chain Attack / Application Security Researchers have identified a dependency confusion vulnerability impacting an archived Apache project…
Apr 23, 2024The Hacker NewsThreat Hunting / Software Security In the high-stakes world of cybersecurity, the battleground has shifted. Supply…
Apr 23, 2024NewsroomCounterintelligence / National Security German authorities said they have issued arrest warrants against three citizens on suspicion of…
Apr 23, 2024NewsroomEnd-to-End Encryption / Privacy European Police Chiefs said that the complementary partnership between law enforcement agencies and the…
Cybersecurity breaches can be devastating for both individuals and businesses alike. While many people tend to focus on understanding how…
Apr 23, 2024NewsroomSpyware / Cyber Espionage The U.S. Department of State on Monday said it’s taking steps to impose visa…
Apr 23, 2024NewsroomNational Security Agency / Threat Intelligence The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw…
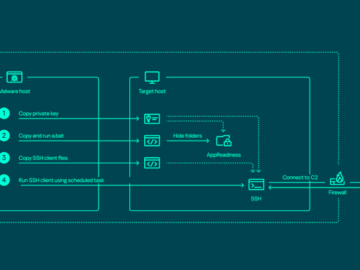
Apr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide range…
Apr 22, 2024The Hacker NewsNetwork Security / Cybersecurity The MITRE Corporation revealed that it was the target of a nation-state…