Category: TheHackerNews
Apr 22, 2024The Hacker NewsNetwork Security / Cybersecurity The MITRE Corporation revealed that it was the target of a nation-state…
Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by…
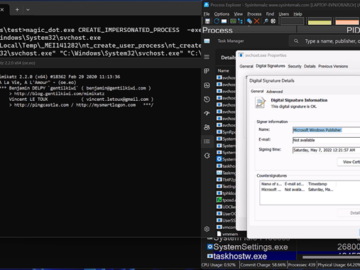
Apr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by…
Apr 22, 2024NewsroomCryptocurrency / Artificial Intelligence Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use artificial…
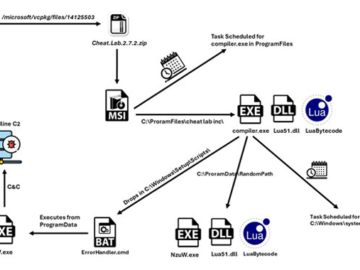
A new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from McAfee Labs reveal….
Apr 20, 2024NewsroomVulnerability / Endpoint Security Users of the CrushFTP enterprise file transfer software are being urged to update to…
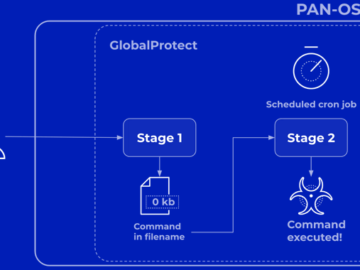
Apr 20, 2024NewsroomVulnerability / Network Security Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS…
Apr 19, 2024NewsroomNetwork Security / Firmware Security Technology, research, and government sectors in the Asia-Pacific region have been targeted by…
Threat actors behind the Akira ransomware group have extorted approximately $42 million in illicit proceeds after breaching the networks of…
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are)…
Apr 19, 2024NewsroomCyber Espionage / Threat Intelligence Government entities in the Middle East have been targeted as part of a…
Apr 18, 2024NewsroomIncident Response / Cyber Espionage Select Ukrainian government networks have remained infected with a malware called OfflRouter since…