Category: TheHackerNews
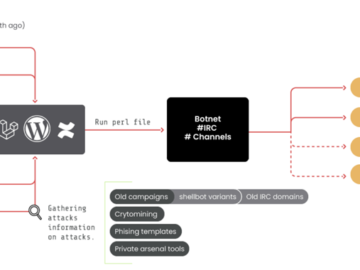
Apr 09, 2024NewsroomBotnet / Crypto Mining A threat group of suspected Romanian origin called RUBYCARP has been observed maintaining a…
Apr 09, 2024NewsroomVulnerability / IoT Security Multiple security vulnerabilities have been disclosed in LG webOS running on its smart televisions…
2023 CL0P Growth Emerging in early 2019, CL0P was first introduced as a more advanced version of its predecessor the…
Apr 09, 2024NewsroomMalware / Cryptojacking Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver…
Apr 09, 2024NewsroomBotnet / Vulnerability Threat actors are actively scanning and exploiting a pair of security flaws that are said…
Apr 08, 2024NewsroomSoftware Security / Cybersecurity Google has announced support for what’s called a V8 Sandbox in the Chrome web…
The ransomware industry surged in 2023 as it saw an alarming 55.5% increase in victims worldwide, reaching a staggering 5,070….
Apr 08, 2024NewsroomCybercrime / Network Security Threat hunters have discovered a new malware called Latrodectus that has been distributed as…
Apr 08, 2024NewsroomCybersecurity / Malvertising A new phishing campaign has set its eyes on the Latin American region to deliver…
Apr 08, 2024NewsroomInvestment Scam / Mobile Security Google has filed a lawsuit against two app developers for engaging in an…
Apr 06, 2024NewsroomSkimmer / Threat Intelligence Threat actors have been found exploiting a critical flaw in Magento to inject a…
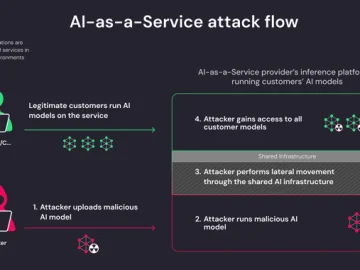
Apr 05, 2024NewsroomArtificial Intelligence / Supply Chain Attack New research has found that artificial intelligence (AI)-as-a-service providers such as Hugging…