Category: TheHackerNews
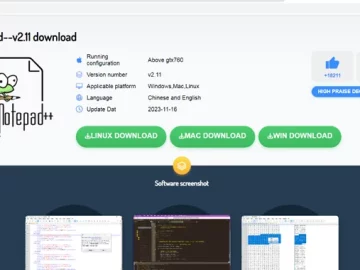
Mar 15, 2024NewsroomMalvertising / Threat Intelligence Chinese users looking for legitimate software such as Notepad++ and VNote on search engines…
Mar 14, 2024NewsroomRansomware / Cyber Crime A 34-year-old Russian-Canadian national has been sentenced to nearly four years in jail in…
Mar 14, 2024NewsroomCyber Espionage / Malware The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called…
Mar 14, 2024NewsroomContainer Security / Vulnerability Details have been made public about a now-patched high-severity flaw in Kubernetes that could…
Being a CISO is a balancing act: ensuring organizations are secure without compromising users’ productivity. This requires taking multiple elements…
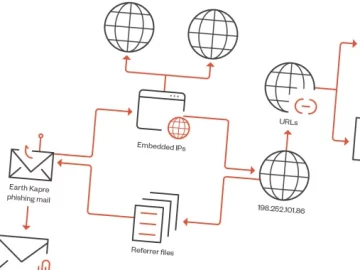
Mar 14, 2024NewsroomCyber Threat / Malware The threat actor known as Blind Eagle has been observed using a loader malware…
Mar 14, 2024The Hacker NewsVulnerability / Network Security Fortinet has warned of a critical security flaw impacting its FortiClientEMS software…
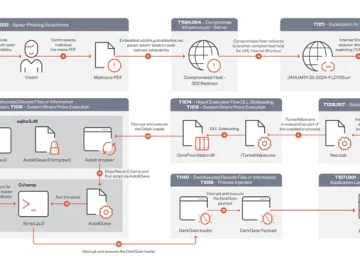
Mar 14, 2024NewsroomMalware / Cyber Attack A DarkGate malware campaign observed in mid-January 2024 leveraged a recently patched security flaw…
Mar 13, 2024The Hacker NewsApp Security / Cyber Security One of the most common misconceptions in file upload cybersecurity is…
Mar 13, 2024The Hacker NewsFinancial Fraud / Mobile Security The threat actors behind the PixPirate Android banking trojan are leveraging…
Mar 13, 2024NewsroomLarge Language Model / AI Security Google’s Gemini large language model (LLM) is susceptible to security threats that…
Mar 13, 2024The Hacker NewsSaaS Security / Webinar Identities are the latest sweet spot for cybercriminals, now heavily targeting SaaS…